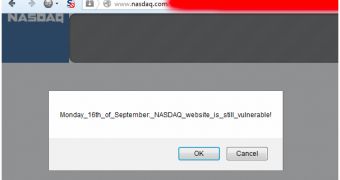
A security expert has identified several cross-site scripting (XSS) vulnerabilities on the website of NASDAQ. Despite being notified, the stock exchange hasn’t done anything to address the issues for three weeks.
According to Graham Cluley, the flaws identified by Ilia Kolochenko, CEO of Swiss-based security firm High-Tech Bridge, could have been exploited for phishing attacks designed to steal sensitive information.
Cluley says that NASDAQ started addressing the issues once Kolochenko took his findings to the press. However, at least one XSS vulnerability still remains.
“The fact that they are vulnerable is not very shocking to me, as approximately 90% of existing websites are vulnerable today. But I was surprised not to receive any Nasdaq acknowledgement of my findings during a three week period, especially taking into consideration their recent technical failure,” Kolochenko commented.
“I think that such important companies as Nasdaq should have a rapid response mechanism to ensure that the IT security team can react quickly, which seems not to be the case today,” he added.
“This means anyone could inject arbitrary HTML code into Nasdaq.com to display a fake web form demanding credit card numbers and other personal information or to inject malware to infect PC users. The only limit is the hacker’s imagination.”
NASDAQ has experienced several cyber security-related issues over the past period. Back in July, the financial organization was forced to shut down the community forum after the website was hacked.
At the time, the attackers might have stolen usernames, email addresses and passwords.
Around one month later, NASDAQ suffered a serious outage that lasted for over three hours. Since initially the organization didn’t provide many details on the incident, experts pointed out that a hacker attack was a plausible scenario.
Later, NASDAQ clarified that hackers didn’t have anything to do with it. On the other hand, the vulnerabilities found by Kolochenko show that there’s still some work to be done as far as cyber security is concerned.
 14 DAY TRIAL //
14 DAY TRIAL //