Grey hats hacking for reputation have turned their attention to websites hosted in the nasa.gov domain name space. Websites administered by two NASA centers were compromised in the last few days through SQL injection attacks.
The first two incidents involve the websites of the Instrument Systems and Technology Division, as well as the Software Engineering Division, operating out of NASA's Goddard Space Flight Center. The grey hat hacker taking credit for these proof-of-concept hacks is a Romanian security enthusiast going by the online handle of TinKode.
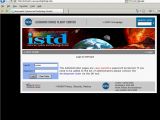
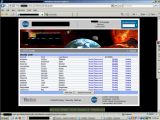
According to information posted on his blog, the hacker located and exploited SQL injection vulnerabilities in both the www.istd.gsfc.nasa.gov and www.sed.gsfc.nasa.gov websites. This allowed him to extract info from the underlying databases.
SQL injection is a common type of attack, which involves the execution of SQL queries under the credentials of the website itself, by manipulating the URL. The results of these queries are usually displayed back to the attacker in the browser window.
As far as the extracted information goes, TinKode went straight for the "access" table, where data about the website's accounts was stored. This included info such as first names, last names, e-mail addresses and passwords. However, the database also contained tables called branch, docs, docsbranch, intro and programs.
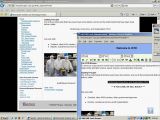
Using login credentials for one of the several accounts with administrative permissions, the hacker showed that he was able to modify the content of the website. As far as his reasons go, TinKode says that he did it "because [he] could, and they were vulnerable."
"I didn’t want to make something bad! Only to show as nasa have many vulnerable subdomains to SQLI, XSS, etc.," the hacker explains. "As you can see, I didn’t change anything," he adds. Both of the affected websites are now offline, an indication that the webmaster is aware of the problems and is working to remedy them.
A third NASA-owned website was compromised through SQL injection by a self-confessed Lebanese grey hat hacker calling himself Idahc. We were informed of this attack directly via e-mail and since it has not yet been fixed, we will refrain from disclosing any details for now.
We can only reveal that the website belongs to a division at NASA's Langley Research Center and that the password hash for the MySQL root account has been obtained. We have contacted NASA about this incident and we will publish more information, as well as related screenshots, once we receive a response from them.

 14 DAY TRIAL //
14 DAY TRIAL //