Taking advantage of the time-to-patch window, cybercriminals are currently leveraging the remote code injection vulnerability in the Bash command line against network-attached storage (NAS) equipment.
These devices are used by both companies for easy access to files and databases, and consumers for personal storage. They run on Linux, which most often has Bash as the default command interpreter.
Since they could be hosting a large amount of data, it is easy to understand the cybercriminals’ interest in compromising them.
Security company FireEye has discovered that this type of incidents are more frequent in Japan and Korea, but are not limited to these regions, as one victim has been observed in the US, too.
“Based on the sheer number of devices which run an embedded Linux OS and the time-to-patch window, we feel the potential for widescale compromise of network-connected personal and business data storage systems is very high at this time. As many smart- or connected-devices utilize similar set-ups, this represents one of the first in the wild Shellshock attack against IoT-type devices,” threat researchers James T. Bennett and J. Gomez say in a blog post.
Embedded devices made by QNAP are most targeted
Products from multiple manufacturers have been attacked, but the security company says that it has evidence pointing to the fact that those from QNAP are particularly interesting for cybercriminals.
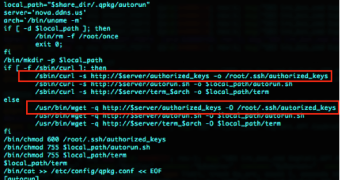
In the observed attacks, hackers try to add their own SSH key to the “authorized_keys” file for future login, and try to install an ELF (Executable Linkable Format) backdoor, which is a binary file for Linux.
The attack vector employed was the administrative page located at “/cgi-bin/authLogin.cgi,” for both QNAP and other devices.
FireEye notes that the incidents observed by their researchers involved QNAP NAS devices belonging to Universities and Research Institutes located in the aforementioned countries.
Hackers try to exploit the Shellshock vulnerability by instructing the affected system to download a malicious script that changes the startup configuration of the NAS, copies the SSH key and funnels in the ELF binary.
According to the researchers, two of the servers hosting the malware are located in Korea and the US. This is the only information about the attackers discovered so far.
QNAP issued patch to plug the hole
FireEye contacted QNAP about the attacks on their products, and at that time, the company released a communication urging its customers to disconnect the NAS equipment from the Internet in order to prevent future hack attempts.
However, if an individual has already compromised a system in the network, they can still gain access to the storage device and exfiltrate sensitive information.
Currently, QNAP has released an update that patches the Shellshock vulnerability on their devices. Users are strongly advised to download and install it.
 14 DAY TRIAL //
14 DAY TRIAL //