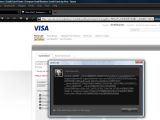
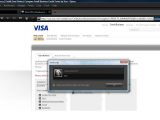
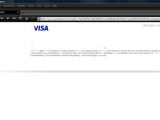
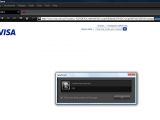
Self-confessed ethical hacking outfit Team Elite has recently reported cross-site scripting (XSS) weaknesses in not one, but four different Visa websites. All of the vulnerabilities allowed attackers to prompt arbitrary JavaScript alerts.
The XSS vulnerabilities were reported by a grey-hat hacker calling himself Methodman, who previously discovered similar bugs in numerous high-profile websites. These latest flaws affected usa.visa.com, visacemea.com, visa.com.ua and visamiddleeast.com, and were found in the country selection form, which seems to be consistent over all of them.
A potential attacker could have exploited these bugs through URL manipulation, in order to force rogue JavaScript prompts with arbitrary content. Such a malformed link could have then been propagated through e-mail and used to launch a phishing campaign.
Being the company that operates the world's largest retail electronic payment network, Visa is also one of the biggest players in terms of developing security standards for the credit card payment industry. Back in October 2008, it issued a Data Security Alert regarding SQL injection vulnerabilities, in which it made several recommendations for mitigating this form of attacks.
The validation of all user input on web-based applications and adopting secure coding practices that include regular independent code reviews are just two of the recommendations made. Even though these referred to SQL injection attacks, they can also be applied to protect from cross-site scripting.
XSS is also caused by failure to properly sanitize user input in web forms and is a sub-category of Web code injection vulnerabilities. This incident stands to demonstrate the prevalence of such bugs, as even the companies that are most aware of them and possible mitigation solutions are affected.
However, Visa is not the only example of a security-aware company overlooking such flaws. Since the beginning of the year, it was revealed that websites belonging to some of the largest antivirus vendors were riddled with similar weaknesses.
"Visa Staff has been alerted about this and we hope they fix them quickly," Methodman wrote in his article on Team Elite's website. Visa can be congratulated, as it did not only fix all the reported problems in a timely manner, but also went a step further. Anyone trying Methodman's proof-of-concept exploit code now will receive a warning that reads, "The URL embedded in the link was not valid. If you suspect that this might be an attempt to get personal information from you, please see the Visa security section on protecting yourself from Phishing attempts by clicking here."

 14 DAY TRIAL //
14 DAY TRIAL //