Mozilla launched a new stable version for the Firefox web browser, implementing support for public-key pinning, a feature that validates the legitimacy of a server based on an internal list of trusted certificates.
Secure communication (SSL/TLS) to an online service is done by encrypting the traffic, based on a digital certificate issued by any Certificate Authority (CA), verifying the identity of the service.
Fraudulent certificates have been obtained in the past by cybercriminals either by tricking a CA into emitting a new valid SSL certificate for a domain or by hacking into their systems and issuing one themselves.
A malicious website verified with a fraudulent certificate could trick clients into believing they communicate with a trusted server and offer crooks the opportunity to intercept traffic intended for the original service.
Cybercriminals also rely on man-in-the-middle (MiTM) attacks, which involve intercepting the traffic between the client and the server. Basically, all communication is done through the attacker’s infrastructure.
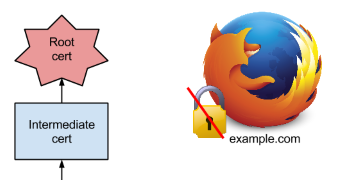
In Firefox, starting version 32, public-key pinning eliminates these risks, as the website’s digital certificate has to match the one present in the web browser, both issued by the same CA.
“If any certificate in the verified certificate chain corresponds to one of the known good (pinned) certificates, Firefox displays the lock icon as normal,” says Sid Stamm, senior manager of security and privacy engineering at Mozilla.
“When the root cert for a pinned site does not match one of the known good CAs, Firefox will reject the connection with a pinning error,” he added.
At the moment, the key pins for the digital certificates for addons.mozilla.org and Twitter are available in the browser. Pins for Google domains are to be added in future versions of Firefox, along with those for other websites.
Google has already increased the security of Chrome through the implementation of public-key pinning back in version 13 of the web browser, in 2011.
This has helped the company keep its users safe from attacks relying on fraudulent certificates.
In August 2011, Google was reported an incident where attackers managed to get their hands on an SSL certificate issued by DigiNotar CA, that worked for any google.com domain. This permitted the cybercriminals to collect the login details to Gmail accounts.
At that time, Chrome users remained unaffected because of the public-key pinning feature having already been implemented in the web browser a few months earlier; connection to the fraudulent websites with Google’s tool caused an alert that the certificate is invalid.
 14 DAY TRIAL //
14 DAY TRIAL //