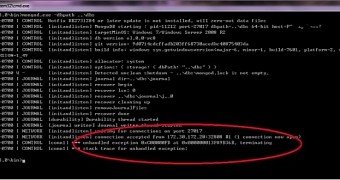
A vulnerability has been discovered in a third-party component in MongoDB that gives a remote attacker the possibility to crash the machine running the database, if they have access to Mongo shell.
The security fault resides in the PCRE library of regular expressions, which is used for database querying and for pattern matching in PERL code.
Outdated PCRE puts servers at risk
MongoDB includes PCRE 8.30, a version released in March 2012 and affected by CVE-2014-8964, which can be exploited to cause a denial-of-service (DoS) condition on the server via a specially crafted regular expression.
Security researchers at Fortinet uncovered the weakness saying that they successfully tested multiple variants of the crash-triggering regular expression.
According to a security advisory from MongoDB maintainers, an attacker would need to be authenticated in order to take advantage of the flaw.
However, the default configuration of MongoDB does not have authentication set up, Fortinet researchers say in a blog post on Saturday, which makes the attack easier to carry out.
Also, there has been reported that plenty of administrators fail to properly secure access to the database machine and leave it accessible over the Internet.
Furthermore, the threat does not require credentials with elevated privileges, as any username and password pair used for accessing the database is sufficient to pull off the exploit.
New MongoDB versions released
To mitigate the risk, the developers have released new versions of MongoDB (2.6.9 and 3.0.1) that integrate a patched build of PCRE.
The priority level for the update has been marked as “major” by the developers, although Fortinet lists it with a “medium” risk.
MongoDB is a very popular NoSQL database used by major websites, such as FourSquare and eBay, which provides the possibility to store and process unstructured data not completely suitable for being managed through MySQL.
 14 DAY TRIAL //
14 DAY TRIAL //