A more complex version of the Svpeng Trojan for Android mobile devices has been identified recently and it appears to have been equipped with ransomware capabilities.
The threat appeared on the security scene about a year ago, and at that time it was considered a standard Trojan-SMS that targeted SMS banking accounts; but it soon started to grow in complexity as the authors switched the target to mobile banking users.
At the beginning of June, however, researchers at Kaspersky Lab discovered a fresh modification for Svpeng that included ransomware features.
Unlike the first mobile encrypting malware (Android/Simplocker - Trojan-Ransom.AndroidOS.Pletor.a) analyzed by ESET and Kaspersky, this one holds the entire device hostage, not just specific files.
It achieves this by locking the smartphone until a ransom is paid. The device will not respond to any actions except for those that lead to paying the money or to turn it off. However, as soon as the device is re-started, the Trojan immediately gains control again.
Similar to Trojan-Ransom.AndroidOS.Pletor.a, the new Svpeng takes a photo of the victim and shows it in the ransom message.
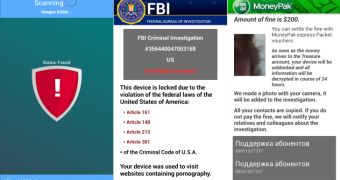
As soon as the device is infected and the malware is deployed, a fake scan is initiated, which, as a result of detecting prohibited content, proceeds to locking the phone because it “was used to visit websites containing pornography,” which is in “violation of the federal laws of the United States of America.”
The ransom is $200 (148 EUR) and victims are provided multiple payment methods, MoneyPak vouchers being one of them. In this case there are several alternatives for buying them in the US.
Kaspersky Lab Expert, Roman Unuchek, writes that unlike the previous variants of the Trojan that targeted Russian citizens, this one focuses on United States residents, 91% of the infections being detected in this area. Other nations where the infection is present are UK, Switzerland, Germany, India and Russia.
The security firm identified a total of seven Svpeng modifications, all including “a Cryptor class reference, but none of them makes any attempt to use it.” However, it could be possible that attackers still have to perfect the encryption capabilities of the threat and release it in the future.
Apart from this, the versions also check the system for the presence of some banking apps and send the findings to the command and control server. According to Unuchek, “cybercriminals are probably just gathering statistics about the use of these apps on infected devices.
“Considering that Svpeng is, first and foremost, a banking Trojan, we can expect to see attacks on the clients of these banks who use mobile apps to manage their accounts.”
 14 DAY TRIAL //
14 DAY TRIAL //