A flaw in Minecraft allows clients to crash the game server by sending them a packet whose parsing exhausts the machine’s processing power, says a researcher who released a proof-of-concept code to back his claims.
According to Ammar Askar, a developer from Pakistan, crashing the system exploits a feature in Minecraft items from the player’s inventory, which allow storing of arbitrary metadata.
When the game starts, it communicates with the server, sending information about the items available in the client.
Complex structure is easy to generate, difficult to parse
Askar has discovered that the metadata is stored in a format that supports complex data structures (NBT - Named Binary Tag), which is similar to JSON (JavaScript Object Notation). By creating a packet that is not easily processed by the server, a client could bring the machine down.
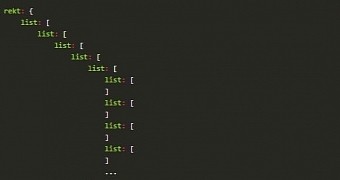
The developer says that crafting a packet of this sort is not difficult, and for demonstration purposes, he created a hierarchical structure of lists within lists, down to five levels.
Such a structure can be easily generated, and the result in Askar’s case was a total of 30 million lists, 26.6 megabytes in size. For efficiency, the inventory data is archived before it is sent to the server, and then decompressed, which means that the machine ends up with the data in the memory.
Parsing the structure is what causes the crash because Java representations of the objects are created, an action that increases the CPU load.
Glitch goes unpatched for almost two years
Askar says that he reported the vulnerability to Mojang, Minecraft’s developer, in late July 2013, when he also provided the proof-of-concept (PoC); the version of the game at that time was 1.6.2. A reply came that the issue was being dealt with.
Subsequent communication with the developer was ignored, Askar said, and in October 2013, he decided to wait for the fix to be implemented. However, after the release of two major versions, the vulnerability was still present in the game.
In a blog post disclosing the flaw on Thursday, Askar said that Mojang did try to come up with a fix but failed because it was not tested against the PoC sent initially.
“A combination of mis-communication and lack of testing led to this situation today, hopefully it can be a good learning experience,” Askar says. He also admits that a warning about going public with the disclosure would have been a proper course.
Minecraft versions affected by the flaw include 1.8.3 and almost all earlier builds.
 14 DAY TRIAL //
14 DAY TRIAL //