A Chinese advanced persistent threat (APT) group relied on Microsoft’s TechNet portal to hide the IP addresses for the command and control (C&C) servers of BLACKCOFFEE, a malware piece used in cyber-espionage campaigns.
The IP strings were published in different threads on the forum, profile pages or comments in encrypted form and were accessed by the malware after compromising a system. The method is also known as “dead drop resolver.”
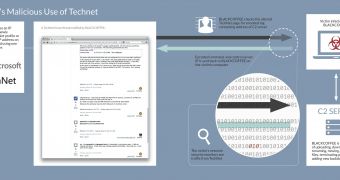
C&C string located between specific markers
Researchers from FireEye and Microsoft Intelligence Center investigated the tactic by locking the pages containing the IPs and sinkholing one of them in order to gain insight into the recent activity of BLACKCOFFEE.
The group behind the campaign has been called APT17 and it is also known as DeputyDog, whose wielding of different BLACKCOFFEE variants has been monitored since 2013.
Its actions have been documented in the past by FireEye, the victims ranging from U.S. government entities to the defense industry, law firms, information technology companies, mining companies, and non-government organizations.
Once BLACKCOFFEE is installed on a computer, it can exfiltrate information as well as add new data, create a reverse shell, and log and terminate the running processes.
According to the analysis from FireEye, the malware includes the links to the TechNet pages containing the C&C addresses. The numerical string is located between two markers, “@MICR0S0FT” and “C0RP0RATI0N,” in an encoded form.
After decoding the address, BLACKCOFFEE communicates with the C&C machine, receiving instructions and delivering stolen information.
Technique likely to be adopted by other groups
By adopting this tactic, DeputyDog delays detection of the systems operated by the threat actor via binary analysis of the malware. As such, even if a target computer is discovered and investigated, the campaign is not stopped and the other infected systems can still be manipulated.
This technique to hide the address of the communication endpoint has been used in the past in cyber-espionage campaigns. The C&C strings have been seen posted even on social media websites such as Twitter and Facebook.
FireEye believes that threat groups may already leverage this tactic with their own variations and warns that others might adopt it in the future.
 14 DAY TRIAL //
14 DAY TRIAL //