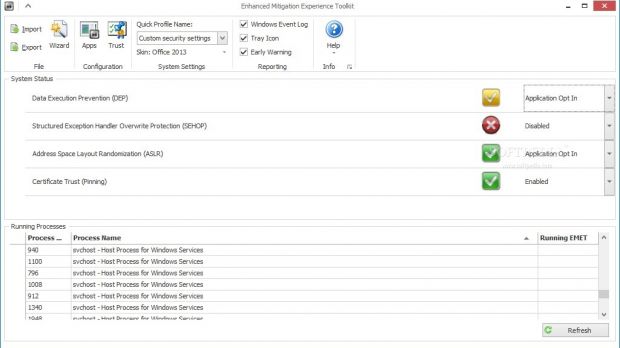
The latest revision of the Enhanced Mitigation Experience Toolkit (EMET) from Microsoft addresses several compatibility issues between Export Address Table Filtering (EAF+) and some programs and hardens the exploit mitigations already available in the product.
EMET is a free security tool widely used in the corporate environment that permits setting up defenses against common and well known attack vectors. It does this through various vulnerability mitigation mechanisms, such as EAF+, which was added in July, in build 5.0 of the tool.
Adds compatibility improvements and memory dumps saving when protection mechanism is triggered
EAF+ is a protection technology designed for the prevention of memory reads, which are regularly used in building vulnerability exploits.
Released on Monday, the new version of the application should no longer generate compatibility problems between EAF and Internet Explorer, Adobe Reader, Adobe Flash, and Mozilla Firefox.
On the same note, Microsoft eliminated the problems caused by interaction with the Internet Explorer Developer Tools and the Manage Add-ons feature in the web browser.
Apart from compatibility quirks, the developer also focused on a potential race condition in the Mandatory ASLR mitigation and improved and hardened several mitigation technologies in order to make them more resilient to bypasses and attacks.
Among the new things added in the release is Local Telemetry, a feature that permits storing memory dumps locally as soon as a mitigation is deployed.
The importance of this option consists in the fact that the memory dumps can be analyzed at a later time and help the admin determine the cause that triggered a mitigation response from EMET.
EMET is no silver bullet for exploits
Updating to EMET 5.1 is recommended especially for clients that have the previous release installed and run it along Internet Explorer 11 on Windows 7 or 8.1, because compatibility problems were uncovered with the security updates for IE in November.
Although EMET is a great exploit stopper, it is not a silver bullet as far as software exploits are concerned as researchers found several times that the tool can be bypassed.
One of the most recent finding is a bug in 19-years-old code available in Windows 95, also used by Internet Explorer 3.0, and which survived undetected until May, this year. With the introduction of VBScript in IE 18 years ago, the glitch became remotely exploitable.
It was reported privately to Microsoft, who issued a fix in this month’s round of updates. Researchers found that it evaded detection from EMET exploit mitigation technologies.
In another report in July, security experts discovered a method to bypass all protection mechanisms in EMET, one after another, in a chain reaction.
However, a compromise via these techniques was no easy feat to pull and no evidence has been found of them being employed outside the test labs.
 14 DAY TRIAL //
14 DAY TRIAL //