Microsoft has taken down one of the 10 largest botnets in the United States and a major source of spam globally. Tim Cranton, Microsoft associate general counsel, made public the results of the initiative referred to internally as Operation b49 on February 24th, after the company made sure that the actions it has taken against the Waledac botnet were successful. In order to take down Waledac, the Redmond giant used a combination of legal action and a technical counterattack.
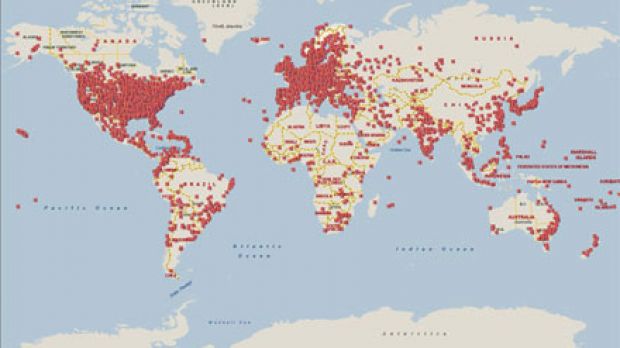
“Waledac is estimated to have infected hundreds of thousands of computers around the world and, prior to this action, was believed to have the capacity to send over 1.5 billion spam emails per day. In a recent analysis, Microsoft found that between December 3-21, 2009, approximately 651 million spam emails attributable to Waledac were directed to Hotmail accounts alone, including offers and scams related to online pharmacies, imitation goods, jobs, penny stocks and more,” Cranton explained.
However, Microsoft did not actually kill Waledac, or managed to remove the malicious code which continues to be present on infected computers. A botnet is an extremely complex organism, not unlike a human body. First, attackers use various techniques and mechanisms, especially social engineering, to infect computers with malware, in this case with Waledac.
However, gone are the days when hackers applied destructive tactics. The attackers behind Waledac are perfectly content with unsuspecting users to continue running their infected machines, even though they are no longer in control. Instead, it is the Waledac authors that are now owning the machine, and can control it remotely, telling it to perform various actions which are hidden from the user, from participating in distributed denial of service attacks, to sending spam, to click fraud and to spreading additional malware. All computers infected with Waledac, and similar malware, are referred to as zombie machines, and they are the body of the botnet. The head is the attacker which moves all zombie computers like pawns via a control server.
What Microsoft did was to cut the connection of the control server from the zombie machines. Specifically, zombie computers infected with Waledac, while still compromised by the malware are no longer under the control of attackers.
“On February 22, in response to a complaint filed by Microsoft (“Microsoft Corporation v. John Does 1-27, et. al.”, Civil action number 1:10CV156) in the U.S. District Court of Eastern Virginia, a federal judge granted a temporary restraining order cutting off 277 Internet domains believed to be run by criminals as the Waledac bot,” Cranton stated.
“This action has quickly and effectively cut off traffic to Waledac at the “.com” or domain registry level, severing the connection between the command and control centers of the botnet and most of its thousands of zombie computers around the world. Microsoft has since been taking additional technical countermeasures to downgrade much of the remaining peer-to-peer command and control communication within the botnet, and we will continue to work with the security community to mitigate and respond to this botnet.”
Three days after Operation b49 started, Microsoft has managed to kill off the connections between the vast majority of Waledac zombie PCs and the control servers. The software giant is now working to make sure that the severed connection remains down.
And while they are no longer under the control of attackers, end users have an opportune moment to make sure their machines are clean. Microsoft recommends either the Malicious Software Removal Tool or Microsoft Security Essentials, both available as free downloads, and both perfectly capable of removing Waledac.
Malicious Software Removal Tool is available for download here.
Microsoft Security Essentials is available for download here.
 14 DAY TRIAL //
14 DAY TRIAL //