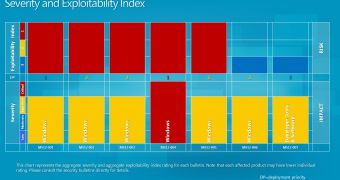
Microsoft released a number of seven security bulletins for January 2012 that address vulnerabilities found in Windows Media, Windows ClickOnce application installer, Windows Object Packager, the operating system’s Kernel, and the now famous SSL/TLS protocol weakness dubbed BEAST.
The vulnerability in the SSL 3.0 and TLS 1.0 protocols isn’t specific to Windows, but since it’s an important one Microsoft addressed the issue to prevent information disclosure.
Discovered in September, 2011, the flaw allows a man-in-the-middle attacker to guess the ciphertext used in encrypted traffic, permitting him to decrypt HTTPS traffic.
If the latest security update is not installed, a cybercriminal could use social engineering to convince a user to execute a specially crafted media file which would allow him to execute arbitrary code and gain the same rights as his victim.
A flaw that exists in Windows Kernel gives an attacker the opportunity to bypass the SafeSHE secutity feature and leverage the structured exception handle to run a piece of malicious code.
Remote arbitrary code could also be executed by a hacker due to flaws that exist in the Windows Object Packager and in the way it loads ClickOnce applications.
In order to take advantage of the vulnerability from the ClickOnce application installer, a cybercrook would have to convince a victim into opening a cleverly designed Office file.
Information disclosure would be possible due to a weakness that affects the AntiXSS library when handling certain HTML files. Besides obtaining information that could help him launch other attacks, a hacker is also able to get his hands on sensitive data such as cookie-based authentication credentials.
A privilege escalation vulnerability permits the elevation of user rights by taking advantage of a security hole in the Windows Client/Server Run-time Subsystem (CSRSS) because of the way a sequence of specially crafted Unicode characters is processed.
Symantec’s Urgency Rating system rates the aforementioned vulnerabilities at an average of 7 out of 10 which means that users are advised to immediately install the update to protect themselves from malicious operations.
 14 DAY TRIAL //
14 DAY TRIAL //