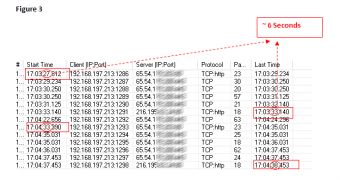
The folks at Websense have managed to prove, once again, that an experienced spammer who attempts to create a large number of Microsoft Live Hotmail accounts to send spam messages doesn't need more than six seconds in order to bypass the CAPTCHAs. The reports comes after only a few days since several sources confirmed that hackers around the world are willing to hire and pay human workforce in order to enter the visual CAPTCHAs and help them create accounts on several services.
Getting back to the Microsoft Live Hotmail CAPTCHA, Websense's experts estimated that 6 seconds should be enough if a spammer who uses advanced techniques attempts to register multiple accounts on this mail service. Just like previous attacks, a bot starts the browser (usually Internet Explorer), connects to the service, uses a pre-defined list of account names and attempts to bypass the CAPTCHAs. The process may take no longer than six minutes, Websense explains.
"It is observed that unlike Live Mail Anti-CAPTCHA and Gmail Anti-CAPTCHA operations in the past, the current attack is aggressive and instantaneous in terms of CAPTCHA breaking host turn-around time. In the current attack, the response time of CAPTCHA breaking host after grabbing a CAPTCHA image from a victims' machine, analyzing it, and responding back to victims' machine with corresponding CAPTCHA code is relatively lower when compared to previous attacks," the people of Websense explained.
What's worse is that a Windows Live Hotmail may also be used for several purposes, other than sending spam email messages. For instance, the same accounts registered through the method described by Websense, can also be used for connecting to Windows Live Messenger, which means another spamming campaign could be started on the instant messaging application, millions of connected users being vulnerable to such an attack.
 14 DAY TRIAL //
14 DAY TRIAL //