The Gamarue worm has been around for quite some time. While it’s not a novelty that the malware can spread from one computer to the other via removable drives, Microsoft experts have uncovered new variants that employ some interesting techniques.
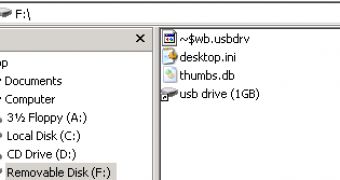
Four components of Worm:Win32/Gamarue are copied onto the infected device, a USB stick for instance. These components are files named “~$wb.usbdrv,” “desktop.ini,” “thumbs.db” and “usb drive (1gb).lnk.”
The shortcut file, “usb drive (1gb).lnk,” is actually named after the removable device and its size. This is an attempt to trick users into opening the file.
When opened, the .lnk file executes the “~$wb.usbdrv,” which is actually a DLL. This DLL file reads the contents of “desktop.ini” and executes it.
“The code contained in ‘desktop.ini’ first tries to download an updated copy of ‘Thumbs.db’, replacing the existing file on the USB drive. It then decrypts the data from ‘Thumbs.db’ and writes it to ‘C:\Temp\TrustedInstaller.exe’,” Raymond Roberts of MMPC Melbourne explained.
When executed, TrustedInstaller.exe file drops a file (Worm:Win32/Gamarue.I) into the “Temp folder and writes this registry entry: HKCU\SOFTWARE\e_magic .
This entry is actually an encrypted version of “TrustedInstaller.exe” and it’s utilized to infect other removable drives.
“The Worm:Win32/Gamarue.I component, which was dropped into the temporary folder earlier, runs the system file %System%\wuauclt.exe and injects code into that process,” Roberts added.
“This injected code reads the data from the registry entry HKLM\SOFTWARE \Microsoft\0022FF03, decrypts it using a 32-byte key stored within the code, and decompresses it using the widely available aPLib compression library.”
This allows the malware to check for removable drives and infect them. However, it’s worth noting that the spreading component is not written to the disk.
Experts believe that this propagation method increases the threat’s chances of remaining undetected.
Additional technical details are available on the MMPC blog.
 14 DAY TRIAL //
14 DAY TRIAL //