Microsoft has released its Security Intelligence Report Volume 12 (SIRv12) to detail some of the most important security-related incidents that marked the second half of 2011.
The study offers some statistical data on the highly dangerous Conficker worm. The figures showed that at its peak, the malicious element infected 7 million computers worldwide.
Experts reveal that in order to propagate, the piece of malware utilizes a clever technique that leverages weak passwords. More precisely, it attempts to access local or network resources by trying out a list of highly common passwords.
The Autorun feature in Windows is also abused by the worm. Reliable security software immediately blocks the cleverly crafted file, so this is not exactly a threat. However, the presence of the malevolent autorun.ini file is an indication of an attack attempt.
The paper also studies targeted attacks launched by cybercriminals. In these types of attacks, individuals or entire organizations are targeted with the purpose of causing damage or stealing classified or sensitive information.
In the more recent attacks that target businesses, the masterminds of the operation rely on cleverly designed spam emails to social engineer unsuspecting employees into downloading a malicious attachment that contains an exploit.
When it comes to malware families, the report reveals that the most notable increase was recorded by the now-infamous Win32/Keygen, the numbers of others, such as Win32/Hotbar, Win32/OpenCnady, and Win32/ShopperReports, having dropped considerably since the beginning of 2011.
In the spam category, the figures demonstrate that the number of unsolicited messages blocked by Microsoft Forefront Online Protection for Exchange (FOPE) has constantly decreased. In December 2011, around 14 billion emails were blocked, compared to January 2011 when more than 35 billion were flagged as carrying threats.
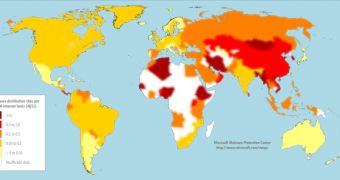
Phishing sites were hosted on free services and compromised sites, most of them being located in Asia and certain parts of Africa.
The complete report is available here.
 14 DAY TRIAL //
14 DAY TRIAL //