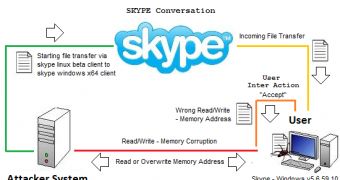
Vulnerability Lab researchers identified a high risk memory corruption flaw that affects the 5.6.59.x versions of the popular messaging applications. By exploiting this flaw, an attacker could remotely crash a computer that’s running Windows 7 simply by sending a file from a Linux client.
The experts demonstrated this vulnerability, found in the file transfer module, by sending a file from Skype v2.2.0.35 Beta for Linux to a contact that was running Skype 5.6.59.10 on a Windows 7 x64 operating system. This transfer resulted in a stable memory corruption on the Windows client side.
“The vulnerability can be exploited by remote attackers with low required user inter action (accept). Successful exploitation requires to accept a file transfer (user inter action) or receive messages & information,” Vulnerability Lab representatives told us.
The security hole, discovered by Benjamin Kunz Mejri, also known as Rem0ve, and Alexander Fuchs, or f0x23, only works on Acer Aspire 5738 notebooks, powered by an Intel Core 2 Duo T6600 processor, running a Windows 7 x64 operating systems.
The bug was reproduced 4 out of 11 times, its successful exploitation resulting in a software and context freeze, and an access violation message.
The vulnerability was identified and reported to Skype in November 2011, the vendor responding two days later. Sometime between November 9 and February 17 the issue was addressed.
The latest Skype version is 5.8.32.154, which probably incorporates the fix for the memory corruption vulnerability. This is why users are always advised to install the latest variants, especially if they come with important security patches.
Vulnerability Lab researchers also identified a buffer overflow vulnerability in Yahoo! Messenger and they showed how a clever attacker can easily make Google+ posts on a user's behalf by tricking him into playing a game.
Skype 5.8.32.154 is available for download here
 14 DAY TRIAL //
14 DAY TRIAL //