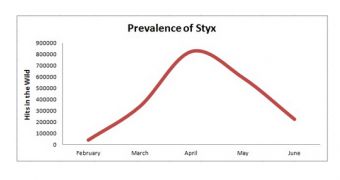
Researchers from security firm McAfee claim to have observed an increase in the prevalence of the Styx exploit kit.
Cybercriminals rely on Styx to redirect the visitors of legitimate websites to a malicious landing page that’s designed to probe potential victims’ systems for vulnerabilities.
If vulnerabilities are found, they’re exploited to push malware onto the impacted devices.
Most of the security holes targeted by Styx are in Java, but Adobe Reader vulnerabilities can also be leveraged to push malware.
One interesting exploit integrated into Styx targets is a TrueType Font parsing vulnerability. This vulnerability was exploited in the wild in November 2011 by the notorious Duqu.
“The final payload of this exploit kit is a downloader that delivers additional malware from the remote server. Depending upon the attacker, the payloads are custom made and delivered to the compromised machine,” McAfee experts note.
Here are additional technical details on how Styx works.
 14 DAY TRIAL //
14 DAY TRIAL //