Since the Shellshock vulnerability in the Bash command interpreter for Linux and Unix systems has been publicly disclosed, operators behind the Mayhem malware have been exploiting it to expand the botnet formed of Linux and FreeBSD servers.
This does not come as a surprise for security researchers, who were expecting this sort of move from the cybercriminals.
Botnet of Linux servers wants to expand
According to Malware Must Die, the attack was initiated from multiple IP addresses of machines already compromised by Mayhem, which scanned the Internet in search for vulnerable systems.
In a thorough analysis of the malware, it was discovered that the infection started with a PHP script that killed all “/usr/bin/host’ processes” and dropped a malicious item named “libworker.so.”
In the recent campaign, the attack has been adapted to Shellshock and a Perl-based remote installer is downloaded and executed; it then runs a malicious binary and then deletes the file, leaving it working in the memory to perform the botnet’s specific operations, a comprehensive post on Malware Must Die says.
The researchers note that the executable process will have the same privileges as the web server daemon.
Mayhem supports multiple modules that allow increased functionality. Its main use is to compromise other servers through various methods, from brute-forcing to exploiting vulnerabilities. Operators can then use it to distribute different types of malware through the websites hosted on them.
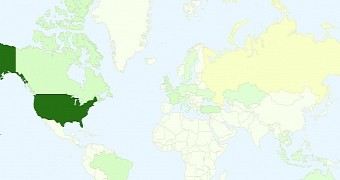
Main source of attacks is the US; detection of the threat is increasing
Mayhem has been thoroughly analyzed recently by security researchers at Yandex. In a report presenting the entry points and capabilities of the malware, they said that statistics collected from two command and control servers showed 1,400 infected machines, most of them being located in the US, Russia, Germany and Canada.
According to data retrieved by Malware Must Die on Friday, the largest number of the attacks in the Shellshock-based campaign was initiated from the US, with 24 IP addresses located in the country.
Cumulated with other regions in the world, the researchers counted a total of 51 sources, from 22 countries, most of them accounting for only one infection. A map with the infections shows the statistics per country.
Initially, the detection of the 32-bit and 64-bit malicious files was quite low in the case of the former, only seven antivirus engines being able to label it as a threat.
However, scan data from Friday shows increased detection, 12 engines being able to recognize the 32-bit binary as a threat, while the 64-bit one generated 24 detections.
 14 DAY TRIAL //
14 DAY TRIAL //