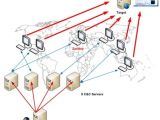
The command and control servers used by the Mydoom variant, responsible for the recent denial of service attacks against Korean and US government websites, receive instructions from a master server located in the UK. Meanwhile, the majority of experts agree that no evidence exists so far to incriminate North Korea.
The existence of a master control server was reported by security researchers from the Vietnamese security vendor Bach Khoa Internetwork Security (BKIS). The company is a member of the Asia Pacific Computer Emergency Response Team (APCERT), which launched an investigation into the attacks at the explicit request of KrCERT.
An analysis of the malware responsible for the recent DDoS attacks that got a lot of media attention revealed that infected computers queried one of eight command and control servers every three minutes, in order to ask for orders. After gaining control of two servers, the BKIS researchers discovered that they were receiving instructions themselves from a single master control server located in the UK.
"The master server is running on Windows 2003 Server operating system. […] We have sent KrCERT and US-CERT the IP address of the attacking source," Nguyen Minh Duc, senior security researcher and security director at BKIS, noted. Furthermore, after inspecting the server logs, the company puts the number of infected computers at almost 167,000, a considerable increase over the previous estimate of around 50,000.
In related news, a U.S Republican congressman urged President Obama to retaliate against North Korea, which was named as the possible source for the attacks. "It's time for America, South Korea, Japan and others to stand up to North Korea," otherwise "Next time they'll go in and shut down a banking system ... or manipulate the electrical grid either here or in South Korea. Or they will try and miscalculate, and people will be killed," Congressman Peter Hoekstra, who sits on the House Intelligence Committee, for The Washington Times' America's Morning News radio show, said.
Graham Cluley, senior technology consultant at Sophos, responded on his blog and pointed out that, "No evidence has been produced showing that the government of North Korea are behind the denial-of-service attacks," explaining that, "A hacker can be based anywhere on Earth and command a worldwide botnet to bombard websites with traffic." The security researcher concludes that, "If Mr Hoekstra has been advised by internet experts that the attacks definitely came from North Korea, I would politely suggest that he finds himself some new internet experts."
AVG's Chief Research Officer, Roger Thompson, agrees and says that, "It was silly to blame North Korea, because the whole point of a ddos from a remote controlled botnet is that no one really knows who's driving it." He does, however, launch another hypothesis about the identity of the attacker – a vigilante.
Apparently, the decision of whoever was responsible to damage the infected systems after July 10 pointed Thompson in this direction. "Why bother nuking 60k computers after doing all the work of assembling them? Nuking them only helps the Good Guys, because the victims are forced to re-build, and therefore clean, their computers. […] The only reasonable explanation for the whole thing is that it was someone who is worried about the botnet problem, and who wanted to make lawmakers think about it, and do something about it," he wrote.

 14 DAY TRIAL //
14 DAY TRIAL //