Back in the day, malware authors needed some serious skills to ensure that their creation remained undetected. Now, experts have found that automated threat analysis systems can be evaded more easily.
Security researches from Symantec explain that malicious elements are designed in a way which allows them to deactivate themselves if they detect the presence of a virtual environment or if they identify a certain process which might be monitoring their actions.
In addition, a piece of malware can suddenly stop its activity by checking for certain registry entries, by checking the video and mouse drivers, by enumerating the system services, by executing special assembler code, or by checking for a certain communication port.
All these elements allow the malware to “tell” if a virtual environment is running or if it’s being monitored by tools usually utilized by security researchers to analyze threats.
These techniques can be leveraged not only to hide its presence from automated threat analysis systems, but also from corporate system administrators who might be looking for malware infections.
One of the more interesting hiding techniques involves the mouse. The malicious element installs a subroutine which monitors the mouse.
When it detects movement or clicks, it steps into play, performing the activities for which it was created. This is based on the principle that people almost always utilize the mouse when they work on their computers.
However, automated threat analysis systems don’t use the mouse, so the malware remains dormant when the mouse is not utilized.
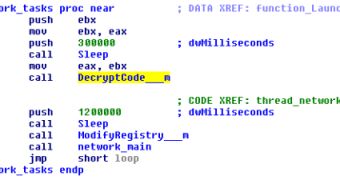
Another clever technique relies on the “sleep” function. Basically, the malicious subroutines are executed at specific intervals.
For instance, there’s a 5 minute “sleep” time before the DecryptCode subroutine (see screenshot) is run. Then, it’s “sleep” again for another 20 minutes before the ModifyRegistry subroutine is executed.
By taking breaks between the execution of each subroutine, the chances for the threat analysis system to scan the file precisely at the time when it’s running a piece of malicious code decrease considerably.
 14 DAY TRIAL //
14 DAY TRIAL //