Researchers from Barracuda Labs discovered a series of malicious emails that allegedly come from Facebook and bear an attachment that’s allegedly available only if Microsoft Silverlight is installed.
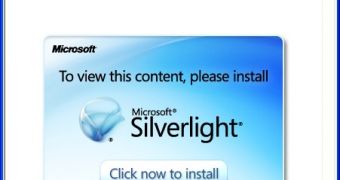
The phony message claims that the user’s account information “has been changed,” but provides no other details, except for a large image that urges the recipient to install Silverlight.
Once the image link is clicked, the victim is served a .pif file from a server located in Malaysia. If run, the pif file, which is similar to executable files, drops a payload identified as Trojan.Win32.Jorik.
Since the entire process is similar to the one in which the legitimate Silverlight is downloaded and installed, the victim may not be aware of the fact that in reality he/she downloaded a keylogger that is designed to steal all the usernames and passwords utilized in web pages and applications.
All the information collected by the malware is stored in a disk file that is sent back to the command and control server, most likely also located in Malaysia.
Internet users are always recommended to be on the lookout for any suspicious emails that may land in their inboxes. Phony Facebook notifications might be much better designed than this one and that’s why it’s important to be skeptical even if the message looks genuine at first glance.
Last, but not least, a good antivirus solution, with an up-to-date virus definition database can, in most cases, protect you even against the most sophisticated threats.
“The easiest way into your computer is to persuade you to push that ‘run’ button. Spammers and malware distributors are constantly looking for ways to convince you to do just that. Be vigilant, don’t be a victim,” Barracuda Labs security researchers advise.
 14 DAY TRIAL //
14 DAY TRIAL //