Last week we learned that an Israeli police department was forced to disconnect all its computers from the public Internet after detecting a piece of malware in their systems. Trend Micro researchers have managed to obtain a sample of the culprit.
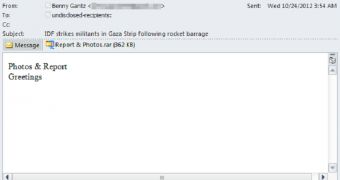
The attack started with an email entitled “DF strikes militants in Gaza Strip following rocket barrage,” apparently originating from the head of the Israel Defense Forces Benny Gantz.
The body of the email didn’t reveal much, except for a short message which read “Photos & Report. Greetings.” The “photos and report” attached to the email were actually a backdoor malware identified by Trend Micro as BKDR_XTRAT.B, commonly known as Xtreme remote access Trojan (RAT).
After analyzing the email’s header, experts learned that one of the targets was an individual from the Israeli Customs agency.
The RAT used in this case is capable of stealing information and receiving additional commands from its remote mastermind.
The latest version of the Trojan has been adapted to target Windows 8 operating systems as well. Furthermore, its audio- and desktop-capturing capabilities have been enhanced and its web browser-stealing abilities have been improved.
Xtreme RAT has been utilized on previous occasions against Syrian anti-government activists.
 14 DAY TRIAL //
14 DAY TRIAL //