Security researchers from BitDefender warn of a new malware distribution campaign which tries to capitalize on the noise caused by Microsoft's latest batch of security updates.
Microsoft releases new security fixes during the second Tuesday of each month, a day that has came to be known in the industry as Patch Tuesday.
Two days ago during the latest cycle, the software giant established a new record by putting out 14 security bulletins (eight critical), which address a number of 34 vulnerabilities in Windows and other products.
It looks like cyber criminals are trying to exploit people's trust in Microsoft, the security industry and the media, which are constantly raising awareness about the importance of updating software, especially the operating system.
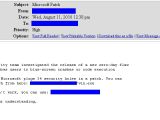
Researchers from BitDefender have intercepted new spam emails with a subject of "Microsoft Patch" which attempt to pass malware as Microsoft security patches.
"Microsoft's security team investigated the release of a new zero-day flaw that exposes Windows users to blue-screen crashes or code execution attacks.
"Because of this, Microsoft plus 34 security holes in a patch. You can download the patch from here: [malicious URL]/win.exe," the rogue email messages read.
The win.exe file is actually an installer for a computer trojan detected by BitDefender as Trojan.SpamBot.CAL. As the name suggests, computers infected with this piece of malware will become part of a spam botnet.
And just in case the first link is taken down by security researchers, the spammers have included a back-up one in the email.
However, the second URL distributes a different trojan called Trojan.Downloader.Agent.ABFG, which is used as an installation platform for additional malware.
"Assuming that their automatic update option is disabled, the official Microsoft website is the alternative recommended download source. So what’s the problem, after all? "It’s KNOWING that updates and patches are not likely to be delivered through e-mails with embedded links, as in the example below," the BitDefender researchers explain.

 14 DAY TRIAL //
14 DAY TRIAL //