An Android app posing as a tool designed to protect information on the device by creating a backup copy actually steals details about the phone and the user activity.
Called SocialPath, one version of the malicious piece of software managed to make it to the official Android store, but Google received an alert from security researchers and removed it.
The distribution model adopted by the cybercriminals is spamming the victim through messages on Twitter and WhatsApp. The link to the rogue app is a short one, created via the Bit.ly service.
SocialPath takes more data than it states
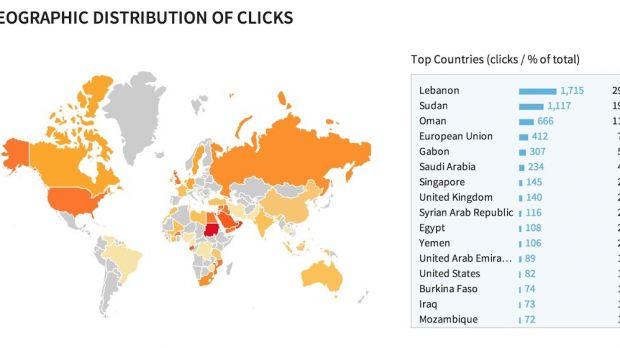
Security researchers at Lookout have analyzed the malicious campaigns and noticed that in one of them almost 6,000 clicks were recorded, most of them coming from Lebanon (1,715). The next two locations were Sudan (1,117) and Oman (666).
Users in countries from the European Union were also deceived to access the link, amounting to 7% of the total clicks.
According to Jeremy Linden of Lookout, SocialPath promises to create safe copies of the contact list, informing that the service would soon be extended to photos, videos and other type of files, and claiming to offer the user access to the data if the device is stolen or lost.
If the recipient of the message decides to enroll for the service, they are asked for the full name, email address, phone number, country of residence, and a personal photo.
This is not the only data uploaded to the command and control server, though, as the app has functions for exfiltrating the list of contacts, stored short text messages and the full call log, which includes phone numbers, datestamp of the call and its duration.
The rogue app can make calls and delete the records
Linden says that the malware authors also integrated the possibility to initiate calls to numbers sent from the command and control server. More than this, the call duration has an expiration time.
“We are unsure what the authors use this functionality for, but we’ve seen similar tactics used as a revenue source — malware authors will call premium numbers to collect associated fees and make money. The malware then deletes the call records so as to hide its activities,” the researcher writes in a blog post published on January 6.
As far as the identity of the operators is concerned, based on the clues found in the app’s code, Lookout believes they are Arabic-speaking individuals.
Given the targeted countries, SocialPath can be an espionage tool with political purposes, but it can very well be part of a more advanced phishing scheme with financial motivations.
Regardless of its scope, Android users should make sure that the apps on their devices are downloaded from trusted sources only and avoid getting them from third-party stores, where content is most of the times posted without previous verification.
 14 DAY TRIAL //
14 DAY TRIAL //