A malicious email campaign delivering the Upatre malware dropper has been discovered by security researchers to affect mostly users in the United States.
The purpose of Upatre is not stealing and plundering sensitive information, but facilitating these activities by downloading and deploying on the system other malware, specifically designed for the tasks.
Classic email theme used to bait victims
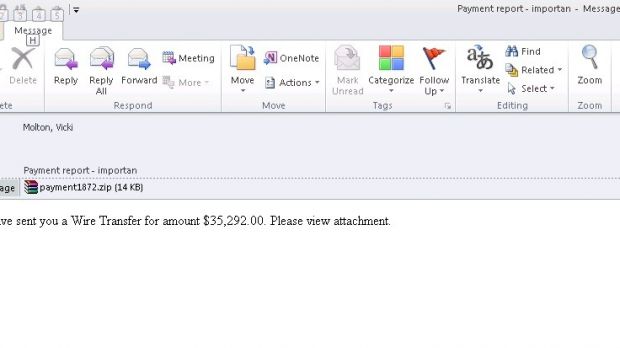
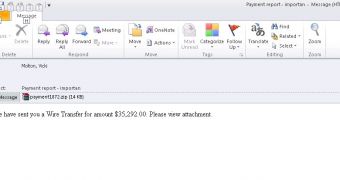
Cybercriminals use the wire transfer notification theme to trick the recipient into clicking the malicious link that downloads Upatre. The incentive is created by informing that a large sum of money has been transferred to the potential victim, with more details being promised in an attached ZIP file.
This is a classic scheme, where crooks use a simple text to pique the curiosity of the receiver of the email and have them launch the malware.
According to security researchers from Microsoft Malware Protection Center (MMPC), the archive contains an item bearing the signs of an Adobe document. A closer look at the file extension, though, shows that it is in fact an executable (SCR).
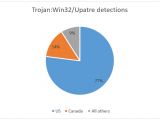
The researchers have monitored the spam campaign and determined that most of the infections, 77%, are present in the United States. Canadians are also affected, but in a proportion of just 14%.
The payload added by Upatre to the computer systems of victims is a variant of a known banking Trojan, which goes by the name of Dyre or Dyreza. Updated security solutions from Microsoft (Security Essentials, Windows Defender) identify it as Dyzap.
Upatre has been seen to connect to two locations to get the threat package, which is available in encrypted form.
Banking Trojan has multiple distribution methods
Dyre Trojan has been involved in numerous malicious campaigns lately, one the latest uncovered by security researchers showing a transition of the communication infrastructure to machines in the I2P anonymization network.
Usually, the distribution is done via Upatre downloader, although cases where the compromise occurred as a result of opening weaponized Adobe or PowerPoint documents have been documented.
Since its discovery in mid-June, Dyre has increased its list of targets, which is composed mostly of financial institutions. However, later variants of the malware also added bitcoin exchange websites and one notable attack focused on the customers of the cloud-based CRM provider Salesforce.
It relies on the man-in-the-middle technique to intercept encrypted communication between the client and the targeted service and routing it through the cybercriminal’s infrastructure. This way, none of the legitimate parties exchanging the secure traffic is aware that the exchange is compromised.
 14 DAY TRIAL //
14 DAY TRIAL //