A malware researcher, going by the online handle of S!Ri, warns that many affiliates for companies selling security software are deceiving users in order to earn install fees. To test this he posted a bogus report about a made-up rogue security application and then watched as others started promoting software that allegedly removed it.
S!Ri is a Microsoft MVP (Most Valuable Professional) and a malware researcher at Malwarebytes. He is also known as the developer of the SmitFraudFix, a popular tool specifically designed to remove scareware and other Desktop hijacking malware. The security researcher also maintains a blog where he documents new versions of such rogue application.
Scareware, also known as rogueware or fake antivirus, is software that uses invasive tactics to trick users into paying for licenses. The vast majority of them scare users by displaying fake security alerts claiming that their computers are infected. In order to mimic professional security programs they also show fake system scans and have well-designed user interfaces.
They then offer the option to remove the inexistent infections, but only if a license code is acquired first. Falling for this trick will not only cost users the amount they pay for a useless license, but also their credit card details, which will end up in the hands of cybercriminals.
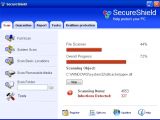
Earlier this month, S!Ri reported on his blog that a new rogueware called "SecureShield" was being distributed in the wild. "SecureShield is the new rogue of the Winisoft family. […] Secure Shield creates random files on the system so it can detect them as infected items," his description said. The malware researcher also included a screenshot of the new threat in action.
After a while S!Ri returned with a new blog post in which he announced that SecureShield was nothing more than a test to expose dishonest security software affiliates. "So I decided to MAKE a picture of a new rogue that does NOT exist: Secure Shield. I post the picture and wait for the 'serious' guys," he explains.
After only ten minutes since announcing the SecureShield rogueware, the test already started to show results. Loaris, a company developing a program called "Loaris Trojan Remover," posted a new entry on its official blog, which claimed to offer cleaning instructions for Secure Shield. Of course, the instructions involved downloading and installing its own product.
"Few minutes later, another webmaster blogs about SecureShield removal: Trojan Killer (a clone of Loaris Trojan Remover)," S!Ri notes. It's worth noting that Loaris doesn't have a very good reputation itself. Back in June, it was caught bundling HiJackThis without authorization in its Trojan Remover installation. HijackThis is a system analysis tool owned by Trend Micro.
And the lying continued with PC Tools affiliates who advertise the company's Spyware Doctor program. S!Ri documented and took screenshots from seven such websites, all claiming to offer free removal of the SecureShield rogueware and linking to PC Tools.
S!Ri concludes that security software downloaded through such affiliates cannot be trusted. "If the downloaded cleaner they link to is installed and registered, they get a retribution. They don't care if the tool can remove or not the infection. They don't analyze the infection. They just make a maximum traffic and try to be ranked on google first page," he writes.

 14 DAY TRIAL //
14 DAY TRIAL //