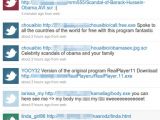
Security researchers warn that multiple spam campaigns detected on Twitter over the weekend target users via replies on topics they employed in recent tweets. Most malicious links spread in this way lead to websites pushing DDoS-capable trojans controlled from Muslim countries.
British antivirus vendor Sophos warned on Saturday that phishing and malware-distribution attacks on Twitter were using the recent international debate concerning the Israeli blockade on Gaza as lure to trap sympathizers on both sides of the fence. Many of these spams pushed a dangerous trojan known as Bifrost, which, amongst other things, can be used to install additional malicious code remotely.
Chester Wisniewski, a security expert with SophosLabs Canada, announced today that Twitter malware-pushing attacks had since intensified in frequency. The spammers use a wide array of techniques, from linking directly to malware, to sending visitors to Web pages riddled with exploits or infected PDF documents.
"Unlike previous Twitter bots that follow many hundreds of users in the hopes that they will follow back, these bots are @ replying to people on topics they are using in their tweets. If you talk about Obama, they @ reply you with a message about Obama and a malicious link," Wisniewski explains. "What surprises me is the range of exploits and malware being used. I have detected plain old trojans that expect you to install them, malicious Java code targeting vulnerabilities from the past year, malicious JavaScript redirects and poisoned document files," he adds.
The researcher speculates that many of these attacks might be attempts from Gaza sympathizers to build botnets for Distributed Denial of Service (DDoS) purposes. This is because five of six malware samples distributed by these latest spam campaigns have command and control servers in Muslim countries like Morocco or Saudi Arabia. In addition, the fact that all samples are variants from the same malware family and all C&C servers are using the no-ip.biz DynDNS provider further suggest a connection between them.
One good piece of news is that spammers made no effort to obfuscate the malicious links via a URL shortening service. This should considerably make it easier for Twitter to block the attacks and identify the offending tweets that were already posted.
You can follow the editor on Twitter @lconstantin

 14 DAY TRIAL //
14 DAY TRIAL //