A new malvertising network, dubbed “Kyle and Stan,” is currently affecting both Windows and Mac users visiting high-traffic locations, such as youtube.com and amazon.com.
The name of the malicious ad network has been given based on the naming scheme used by the attackers. Researchers from Cisco’s Talos Security Research found that hundreds of websites included “kyle” and “stan” in sub-domain strings.
Unique malware piece for each user
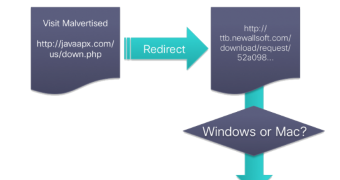
Malvertising functions this way: an attacker manages to insert their malcrafted ad in the stream of an online advertising network which then distributes it to different websites.
When the potential victim clicks on an ad, they are taken to another site, where malware is served and the user is duped to install it via social engineering.
In the case of “Kyle and Stan,” there are multiple variations, but they all follow the above mentioned pattern, the redirect to the payload being done based on the user agent of the visitor’s web browser.
“We observed that Windows and Mac users get redirected to different malware in order to infect both operating systems,” Armin Pelkmann, Talos threat researcher says in a blog post.
The type of threats the researchers found to be served to the victims range from adware and spyware to browser hijacking software, but other types of malware could also be leveraged by the attackers.
Another interesting part is that each victim is delivered a piece of malware with a unique configuration file, thus generating a single checksum, which makes the threat more difficult to detect.
After analyzing some samples, the researchers noticed that the malware droppers also relied on encryption to obtain a different checksum for each threat.
700+ websites affected by “Kyle and Stan” malvertisements
According to telemetry data, more than 700 websites have been impacted by the bad ads, which offer cybercriminals access to an extremely large number of potential victims.
Pelkmann says that apart from YouTube and Amazon websites, the attackers managed to insert their advertisements on ads.yahoo.com, WinRAR.com, as well as javaapx.com, javaupdating.com and grooveshark.audio-updates.com.
The network providing the malicious content has not been identified by Cisco’s security division.
The researchers compiled a list with 74 domains, which they believe have been affected by “Kyle and Stan” malvertising at different times.
They started tracking this network on May 5 and observed intense activity in mid June and early July, but attacks are still occurring at this time.
Since so many domains are involved, the attackers can use one for just a short period of time and then move to another, a tactic that also leads to evading detection.
“All in all we are facing a very robust and well-engineered malware delivery network that won’t be taken down until the minds behind this are identified,” the Cisco blog post concludes.
 14 DAY TRIAL //
14 DAY TRIAL //