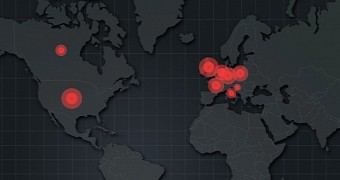
At least 50 million users could be impacted every month by a malvertising campaign distributed through popular online locations like the website of CNN Indonesia, of the airport in Prague, the Bejeweled Blitz Game on Facebook, and RTL Television Croatia.
The distribution of the malware is done via the OpenX advertising platform, where cybercriminals infiltrated advertisements laced with malicious code that redirects to a site hosting Angler exploit kit.
Old glitch in Flash leveraged to spread ransomware and ad-fraud tools
Researchers at Websense say that the injected code is evasive and stealthy, as it is activated only once every 24 hours for each IP address. Also to avoid detection via automated tools, the malicious code is not delivered every time an advertisement is requested.
Users at risk are those with an outdated version of Flash Player, vulnerable to CVE-2015-3090, a glitch that was fixed by Adobe on May 12, with the release of version 17.0.0.188.
Infections via malvertising take place silently during so-called drive-by download attacks, with the user being completely unaware that their computer is compromised.
According to OpenX, its advertisements record over 100 billion impressions every month, making it highly appealing for malvertising campaigns.
Websense says that the operation was first spotted in April and the payloads delivered range from ransomware (CryptoWall) and ad-fraud (Bedep) to backdoor and malware downloaders (Necurs).
Simple infection chain, computers used as proxy
Another threat observed by the researchers is Bunitu, which turns the compromised machine into a proxy for cybercriminal activity, a strategy often used to hide the traces pointing to the origin of an attack.
Unlike in the case of other malvertising operations, the infection chain is simple and there are no extra redirects to throw security experts off the scent.
When the user with an exploitable version of Flash Player lands on a website serving a compromised ad, the redirect is straight to the site hosting Angler, which then drops the exploit, causing the download of the malware pieces.
Most of the affected users are from Europe, but there is evidence that the attack also impacts people in the US, at a smaller scale.
 14 DAY TRIAL //
14 DAY TRIAL //