A zero-day vulnerability in Unity Web Player can be exploited by attackers to retrieve personal messages received by a victim via Gmail or Facebook, as well as read information from the hard disk.
Available as a browser plugin, Unity Web Player is used for rendering 3D content from games created using the Unity cross-platform engine directly in the web browser.
The component is available for Windows (Internet Explorer, Firefox, Chrome, Safari, Opera) and OS X (Firefox, Chrome, Safari); the number of worldwide users is about 600 million, according to the company, but this includes players from all supported platforms.
Cross-domain policy tricked into accessing unauthorized resource
Security researcher Jouko Pynnönen from Klikki Oy in Finland found in 2014 that a security vulnerability in the player can be exploited to bypass restrictions imposed by the cross-domain policy (as defined by the crossdomain.xml file), thus allowing access to content from a different domain than the original one.
Pynnönen explains that retrieving content from a different domain can be done with a malicious Unity app served from the domain of the attacker, which requests content from a different source that is not regularly allowed.
If the app makes a request to a permitted URL that redirects to a targeted site like Facebook or Gmail, the browser then loads the resource and logs in using the stored user credentials. To achieve this, the redirect must contain a location header formatted like this: “http://attacker.site:[email protected]/.”
“The URL refers to ‘target.site’ so the redirect should be denied. However, the Unity Web Player plugin allows the redirect because of the confusing user:password part,” the researcher explains, adding that the risk is much greater in Internet Explorer because the attacker could read local files.
Unity fails to reply to multiple bug reports
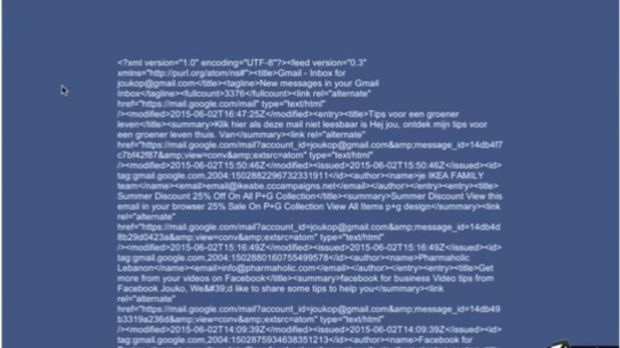
An exploit was created (video embedded below) to demonstrate how the vulnerability can be used to retrieve the victim’s emails.
Pynnönen said that he tried to contact Unity Technologies since December 2014 via email, the web contact, and twice using the bug reporting system, but received no answer until June 3, 2015.
The company should release a patch and is working to improve its security response procedure.

 14 DAY TRIAL //
14 DAY TRIAL //