Cybercriminals often disguise malware as updates for Flash Player. An interesting example has been analyzed recently by security experts from Zscaler.
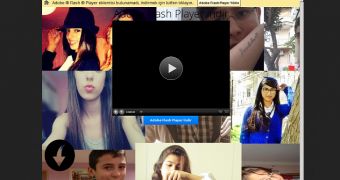
The attack starts with a number of websites that redirect their visitors to click-videox.com. Once victims land on this site, they’re urged – in English or Turkish – to update their Adobe Flash Player in order to see a video.
The interesting thing about this particular attack is that the malicious Flash Player update is actually stored in a Dropbox account.
Two executable files have been spotted by experts: FlashPlayer.sfx.exe and Videonuizle.exe.
Once executed, the malicious files try to disable the Windows UAC, the firewall, the antivirus and other security features.
Ultimately, a variant of the notorious Sality virus is dropped onto victims’ PCs. While the malware itself is flagged by most antivirus solutions, the initial .exe files are detected only by a handful of products.
The campaign appears to be highly successful. Zscaler found that the malicious website was visited by over 1,400 users in a single day.
 14 DAY TRIAL //
14 DAY TRIAL //