A security researcher created a backdoor specifically for drone devices that can interact silently with the drivers and sensors of the flying gadget, allowing the hijacker to take complete control.
Successful attempts at achieving these results have been recorded in the past, Samy Kamkar’s SkyJack project being one of the most notable ones.
The hacker modified a Parrot AR.Drone 2 to search for the wireless signal of other drones and hijack their connection in order to feed them commands from the attacker.
Basically, SkyJack would allow an attacker to create their own army of drone bots, which can be controlled for malicious purposes, or simply for stealing them.
Control software is replaced with malicious one
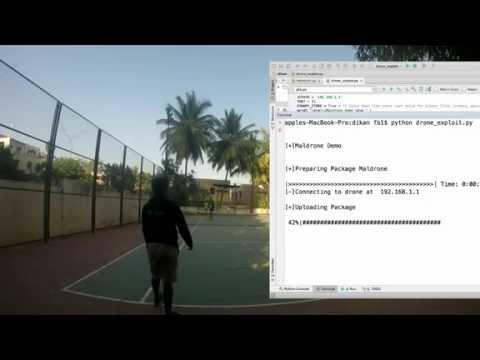
Security researcher Rahul Sasi created a backdoor he named Maldrone that can be planted on a flying device and permits interaction with the navigation board through serial ports used for communication to rotors and LEDs, motor driver, as well as accelerometer, gyrometer, and sonar sensors.
This is done by compromising the software application (program.elf) that controls the device, making it to directly communicate through proxy serial ports set up by the attacker. The infection process also entails redirecting the legitimate communication channel to fake ports.
All this is possible because the manufacturer does not apply any security against replacing the software on the quadcopter.
Sasi explains in a blog post that Maldrone can intercept and modify data on the fly and it is persistent against resets to factory defaults.
He says that the backdoor has been developed for drones based on ARM processors running Linux, but he experimented only with Parrot Ar Drone 2.0 and DJI Phantom.
Not all drones can be infected
However, it is important to note that dropping the payload on some quadcopters cannot be done wirelessly but only when they are connected to a computer.
As such, infecting other gadgets via a wireless connection, as it would be possible via Samy Kamkar’s SkyJack project, cannot be done on all makes and models.
Sasi demonstrated the result of his research in a YouTube video, where he shows how a Parrot Ar Drone 2.0 was hijacked via Maldrone while flying on auto-pilot.
Since the original controller program needs to be terminated in order to be patched, all communication to the rotors is interrupted until the malware takes control; this would mean that for the split second required for the takeover, all functions of the device cease, causing it to drop.
If the drone is high enough in the air, then the rotors may have sufficient time to start again and keep the device flying.

 14 DAY TRIAL //
14 DAY TRIAL //