An independent security assessment of UC Browser for Android revealed serious issues in recent versions of the web browser, including leaking personally identifiable information (PII).
Researchers at Citizen Lab undertook the effort at the request of the Canadian Broadcasting Corporation (CBC), following references to the insecurity of the product in the NSA secret documents provided by Edward Snowden.
The browser is developed by UCWeb, acquired by Alibaba in June 2014. The Android version is listed in Google Play with at least 100 million installs, but the user base of the product on all platforms exceeds half a billion. It is the most popular browser in China and India, but users in other regions have also expressed a preference for it.
Identifiable info and geolocation data sent in the clear or weakly encrypted
The researchers focused on the English and the Chinese variant of the web browser, downloaded in April and March 2015, respectively, and found that both of them transmitted PII either in plain text or using encryption that could be easily broken.
From the two versions, the Chinese one emerged as posing more privacy risks as it also retained browsing information even after the user cleared the application’s cache.
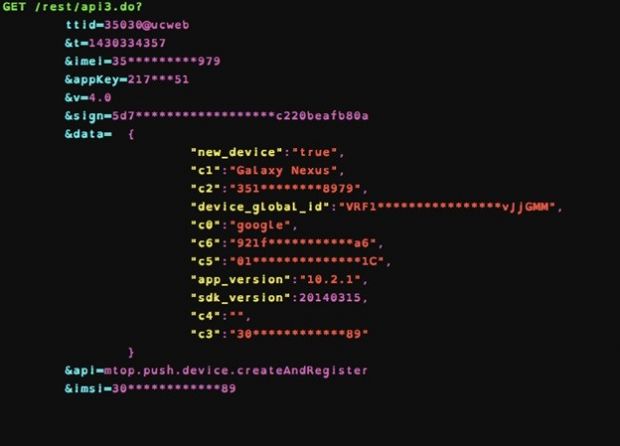
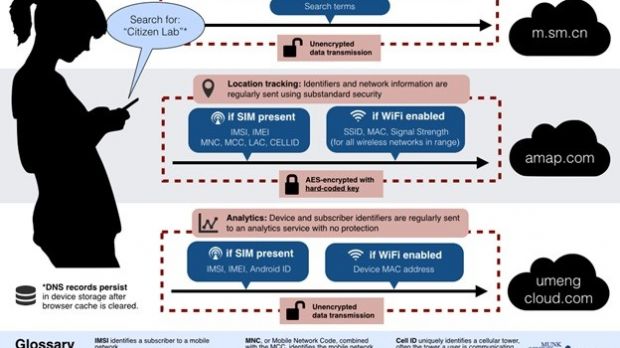
Furthermore, data such as IMSI (international mobile subscriber identity), IMEI (International Mobile Station Equipment Identity), Android ID and MAC address of the device was sent in the clear to Umeng analytics tool from Alibaba.
The same occurred when geolocation data (longitude/latitude and street name) was transmitted by Alibaba’s mapping tool AMAP.
Highly important is the fact that the browser delivered this data while in idle state, without any other intervention from the user than launching it on the device.
On both editions, UC Browser delivered search queries without encrypting them to the default search engines (Yahoo! India and Google for the English variant, and Shenma on the Chinese one).
A consequence of this insecure method for data transmission is that anyone intercepting the traffic from a user could view it with little effort or none at all. The information could be used to identify the UC Browser user, track their movement and gain insight into their browsing habits, allowing for devising more efficient cyber attack methods.
Update does not fix all the issues
Citizen Lab informed Alibaba and UCWeb of the findings and received a reply stating that security engineers would investigate the problems. However, the researchers received no communication from the Chinese developer since May 19, despite “repeated efforts to contact them,” and proceeded to publish the security report on Thursday, May 21.
Two days before disclosing their findings, the researchers tested the UC Browser (Chinese) for Android once more, using a newer version, which is the current 10.4.1.576, and discovered that improvements had been made.
“This version does not appear to send location data insecurely to AMAP as described in this report. However, the issues we describe in this report relating to insecure data transmission to the Umeng component, as well the lack of encryption on search queries, remain in this version,” says Citizen Lab.
These problems have not been solved, as the developer offers the same version for download from its website. The English counterpart, on the other hand, received an update today, to build 10.5.0.575.
 14 DAY TRIAL //
14 DAY TRIAL //