In the attempt to make security as tight as possible, it seems as Mac OS X Lion developers forgot to secure the most basic things. Hashes can be easily obtained and the current user password can be modified without a problem, as no authentication is required.
The guys at Defence in Depth realized that the shadow files which should be accessible only to root users are actually available for anyone. They cannot be accessed directly by non-root users, but by extracting the data from the Directory Services.
If someone wants to check out a directory services listing, they won't obtain much information by typing the /Local/ path, but if the /Search/ path is specified, the results weigh as much as gold for someone with physical admission to the device.
Anyone with a certain amount of knowledge can easily obtain the password of others even if he doesn't have administrator privileges.
A simple program can decode the hashes and turn them into a clear countersign.
There is a small chance that you won't find sensitive information in the shadow file, but that doesn't mean that you cannot do any harm, as using the same /Search/ path while typing a “$ dscl localhost -passwd /Search/Users/john” command, you can easily change John's password without being prompted for the old one.
CNET teaches us how to protect our accounts in this situation as there are some small tweaks you can do in order to properly secure it.
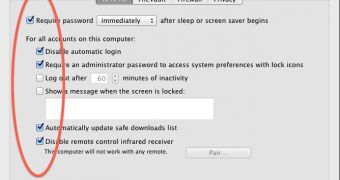
First of all, you can disable automatic log-in. This means that every time you restart the system you'll have to type your credentials. It might bug you a bit, but at least you'll know no one can take over your account.
Sleep and screensaver passwords are always a solution. This way, if you leave your computer unattended for a short while, you can be sure that no one will fiddle with it while you're gone.
Also, by properly managing the users on a certain device and by disabling guest accounts, you can limit the access of others to system components that might give them the opportunity to cause damage [via].
 14 DAY TRIAL //
14 DAY TRIAL //