The distributed denial-of-service (DDoS) business of hacker group Lizard Squad is starting to fall apart as the website managing the attacks has been hacked and the list of registered users exposed.
Lizard Squad has been involved in attacks against Sony PlayStation Network and Microsoft Xbox Live, having knocked offline the two gaming services more than once. The latest incident of this sort happened on Christmas day last year and it served a different purpose than denying gamers access to the community.
Customer information was not protected
Since then, the hackers set up a DDoS service, called Lizard Stresser, that can be rented by anyone to bring down any online target they choose. Thousands of websites have been impacted by attacks carried out through the service.
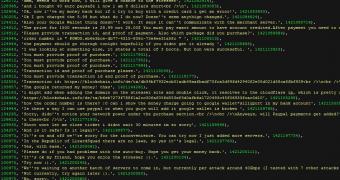
Security blogger Brian Krebs reports that the individual who hacked Lizard Stresser’s website managed to get the database with the customers and the transactions they made to rent the service.
It appears that the members of Lizard Squad did not bother to apply any sort of protection for the database containing client data, and username and password information was stored in plain text.
This may not appear to be too relevant because the registration process accepts any string of characters as username and password. As such, clients are free to provide bogus details.
However, this may not be the case for all customers and some of the less savvy ones may have given a real email address, connecting them to the DDoS incidents they rented Lizard Stresser for.
Hackers made quite some money with their service
According to Krebs, who received a copy of the database, the website stressing tool had more than 14,000 registered users and a few hundred of them paid to use it.
It appears that the hacker outfit made more than $11,000 / €9,500 in bitcoin digital currency since the service was launched in late December 2014.
Among the websites suffering from downtime due to Lizard Stresser, there was Krebs’ own blog, as well as the anonymous image board Infinite Chan (8chan).
After being released to the public, it was revealed that Lizard Stresser relied on a vast network of compromised home routers; access to the devices was obtained because of their poor protection, which had the default credentials provided by the manufacturer to restrict access to the administration console.
 14 DAY TRIAL //
14 DAY TRIAL //