Back in November 2013, Symantec revealed identifying a Linux worm capable of infecting a wide range of Internet-enabled devices, including security cameras, routers, set-top boxes, printers and industrial control systems running Linux.
In January, Symantec spotted a new variant of the worm dubbed Linux.Darlloz. Experts say that a total of over 31,000 devices have been infected with the threat.
The author of Darlloz is constantly updating the code and adding new features to his creation. The worm is designed to infect computers running Intel x86 architectures, but it’s also capable of infecting devices running MIPS, ARM, PowerPC architectures. Routers, set-top boxes and other devices usually have this kind of architecture.
Based on its investigation, Symantec has determined that the main goal of Darlloz is to abuse infected devices for crypto-currency mining. Once it’s installed on a computer, the worm installs open source mining software (cpuminer).
At the end of February, the attackers mined over 42,000 Dogecoins ($46 / €33) and 282 Mincoins ($150 / €108). This isn’t much, but experts expect the attacker to evolve in the upcoming period.
It’s worth noting however that the crypto-currency mining component is only installed on devices with Intel x86 architecture. One explanation as to why the miner isn’t running on “Internet of Things” (IoT) devices is the fact that they don’t have the processing power required for such operations.
Researchers believe that the cybercriminals are focusing on mining Dogecoins and Mincoins because unlike Bitcoins, they can be mined on home PCs.
When it comes to targeting IoT devices, Darlloz uses 13 username/password combinations to access them. Earlier versions only relied on 9 default or common credential sets to access devices.
Currently, the Linux worm only targets IP cameras, computers, set-top boxes and routers, but it could one day be improved to target wearable technology and automation devices as well.
Symantec has gathered some information regarding current infections. Experts have identified a total of 31,716 IP addresses that open port 58455 (on which Darlloz communicates) and host malware files on static paths.
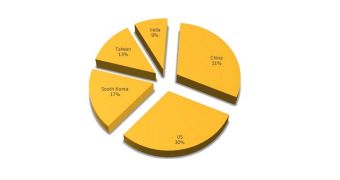
The infections are spread out across 139 regions. Most affected are China, the US, South Korea, Taiwan and India. These countries account for 50% of all infections.
43% of infected devices are computers or servers (Intel-based) running Linux. Printers, cameras, set-top boxes, routers and other smart devices represent 38% of the total number of infections. The large number of impacted IoT gadgets is due to the fact that users seldom scan them for malware.
 14 DAY TRIAL //
14 DAY TRIAL //