Experts continue to analyze the pieces of malware used in the attacks against several high-profile South Korean organizations.
Up until now, no one was able to find a connection between the wiper malware used to delete information from the affected systems and the Whois hacker team that defaced the website of network provider LG U+.
However, F-Secure experts report that they might have found the missing link.
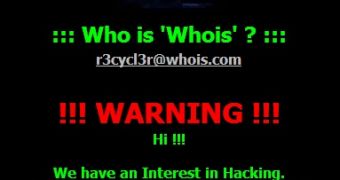
While analyzing the wiper malware samples, they’ve come across one variant that searches for web documents – such as .html, .aspx and .php – and replaces them with a file that contains the Whois Team defacement page.
The timestamp from this particular piece of malware is similar to the one from other wiper samples. However, the malicious element utilized for the defacements uses a different technique to erase the infected drives.
“Unlike the other variants, this sample does not use the strings HASTATI, PRINCIPES, etc. when wiping the file system,” F-Secure researcher Broderick Aquilino explained.
“This time it overwrites the files with zero's, rename them to a random filename before finally deleting them. It also avoids files found in Windows and Program Files directory. All this make sense because the attacker needed the infected webserver to continue hosting the defaced pages.”
The expert believes that the attacks are connected, but the ones that involved the defacement might have been carried out by a different member of the group.
In the meantime, cyberattacks against organizations from South Korea continue. On Tuesday, the websites of several local media outlets that focus on reports about North Korea, and the ones of North Korean defectors were disrupted.
While Pyongyang remains the main suspect, Seoul has avoided naming anyone as being responsible for the attacks.
Here is a video of the defacement pages created by the malware:
 14 DAY TRIAL //
14 DAY TRIAL // 