Hackers using a Twitter profile described as belonging to Lizard Squad claimed responsibility for a cyber-attack that resulted in a complete takeover of the lenovo.com domain and access to emails received by Lenovo employees.
The incident occurred on Wednesday and exposed users trying to access lenovo.com to a slideshow featuring a young girl in front of a computer webcam, with the song “Breaking Free” from High School Musical playing in the background.
Risk associated with the attack is significant
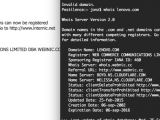
The hackers managed to log into a Lenovo account at registrar Web Communications Ltd. and changed the name server records on Wednesday to point to a server controlled by the attacker, which had probably been compromised to deliver said slideshow.
Lenovo servers were not compromised in any way, but the risk of such an attack is significant because the perpetrators could have served malicious software this way, making it look as if it came from Lenovo.
The new DNS information pointed to a site behind the CloudFlare network, as security expert Jonathan Zdziarski showed in a tweet.
The Twitter profile used to claim the attack has been set up recently (the first tweet came on Sunday) and it appears to be controlled by a Lizard Squad member.
On Wednesday, it posted a message that read: “We're breaking free! Soarin', flyin', there's not a star in heaven that we can't reach!”
Hackers intercepted company emails
Later, the hackers published a couple of emails delivered by an external PR to several Lenovo employees. One of the messages directed the recipients to The Verge’s account on the hack.
This means that the attackers also managed to change the MX mail server records, routing communication through an infrastructure they controlled, thus being able to intercept the emails. Lizard Squad claims that it possesses more emails from Lenovo and says that the stolen info will be checked “for more interesting things.”
Superfish incident was the trigger, hackers have done it before
It appears that the attack is in relation to Lenovo’s blunder regarding pre-installation of the Superfish software on its notebooks for consumers, which signed all HTTPS websites with a root certificate of its own in order to inject ads in web pages; the bigger problem was that a single certificate was used, with an RSA private key that could be easily cracked.
When the mistake came to light, Lenovo moved quickly to mend things up, initially publishing manual instructions for removing Superfish and the rogue root certificate. At a later time, the company announced the availability of an automatic tool that accomplished the task.
In a statement to media outlets, Lenovo acknowledged it fell victim to a cyber-attack that redirected traffic to a machine it did not control. At the moment, the website has been restored and visiting it shows the original content from Lenovo.
The hackers' Twitter account that leaked the emails from the company recently announced another DNS hijack incident that affected the localized Google Search service in Vietnam.
There's your problem, @lenovo. pic.twitter.com/H4uIstGnoe
— Jonathan Zdziarski (@JZdziarski) February 25, 2015
 14 DAY TRIAL //
14 DAY TRIAL //