The support site of leading Chinese PC manufacturer Lenovo has been compromised by unknown attackers who injected a rogue IFrame into the pages over the weekend. Security researchers warn that unwary visitors looking for drivers are exposed to several exploits that install the Bredolab trojan onto their computers.
According to a report from Vietnamese antivirus vendor Bkis, the pages have been infected since at least Sunday afternoon. However, some users have been reporting getting antivirus warnings when visiting Lenovo's download website since Saturday.
The IFrame points to an exploit kit hosted on a domain called volgo-marun.cn. After performing several checks to determine what vulnerable software they had installed on their computer, the visitors were served with exploits tareting older versions of Internet Explorer, Adobe Reader or Adobe Flash Player.
"These exploit codes attempt to load file hxxp://volgo-marun.cn/pek/exe.exe which is a virus, onto victim’s computer. The virus is a new variant of Bredolab Botnet […]. After being loaded onto the computers, the virus copies itself as %Programs%\Startup\monskc32.exe and receives commands from C&C server with domain sicha-linna8.com," Le Minh Hung, senior security researcher at Bkis, writes.
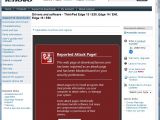
At the moment, the malicious executable is detected by only ten of the 41 antivirus products listed on VirusTotal. The entire download.lenovo.com subdomain has been blacklisted by Google's Safe Browsing service. This means that Firefox or Chrome users should see malware warnings when opening resources hosted on it.
"Of the 46 pages we tested on the site over the past 90 days, 39 page(s) resulted in malicious software being downloaded and installed without user consent. The last time Google visited this site was on 2010-06-20, and the last time suspicious content was found on this site was on 2010-06-20. Malicious software includes 1 trojan(s). Malicious software is hosted on 1 domain(s), including volgo-marun.cn/," a detailed explanation of the Google warnings reads.
Even though the malicious .cn domain appears to be dead at the moment, it could return back online at any time. Therefore, users are advised to stay clear of the Lenovo support website for a couple of days, until the manufacturer has a chance to clean it up and plug the hole that allowed the compromise in the first place. You can follow the editor on Twitter @lconstantin

 14 DAY TRIAL //
14 DAY TRIAL //