Laptop computers from Lenovo featured a browser add-on that installed a self-signed root certificate, giving it the possibility to process traffic that should be encrypted only between the client and the server.
Root certificates identify the Root Certificate Authority, a trusted entity issuing digital certificates to other parties in order to establish a chain of trust online.
They are part of the public key infrastructure scheme and are at the top of the digital certificate tree, holding the private key used to sign other certificates.
Same private key used on all affected Lenovo computers
Superfish Visual Discovery, the add-on present on Lenovo’s products, is designed to provide alternative results for products that may be available at a lower price than the ones searched by the user, based solely on image analysis.
The add-on was found to inject JavaScript into web pages in order to provide advertisements.
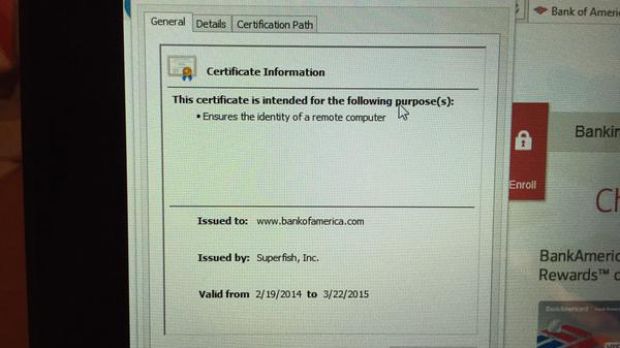
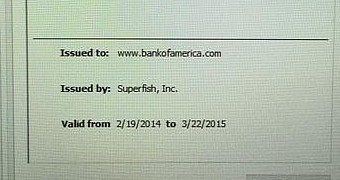
Google security engineer Chris Palmer discovered that Superfish generates self-signed certificates for any encrypted connection, including those intended for banks. The researcher captured an image with an automatically generated Superfish certificate issued for Bank of America.
Basically, the traffic encryption and decryption process is handled by Superfish and then served to the appropriate party.
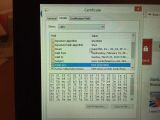
Even more disturbing is the fact that Palmer found that all the root certificates issued by Superfish share the same private key on every Lenovo machine; if the private key is extracted, a malicious actor could intercept and decrypt the secure traffic from machines with Superfish by taking control of an Internet gateway in a public location.
Certificate can be removed manually or by installing stock OS
Mark Hopkins, social media program manager at Lenovo, says in a forum post published in January that the add-on relies only on image analysis technology and it does not collect text strings that would help identify the product.
The entire process is completely automatic and looks in over 70,000 stores for the best offer for the user, Hopkins said.
Despite assurance from Lenovo’s representative that Superfish does not access any other information than images and that it does not profile the user or monitor their online behavior, the fact remains that it is a third-party service that handles private communication between the client and the online service they call.
Hopkins said that Superfish was temporarily removed from the consumer systems until a software build emerges with a fix for the issue. “As for units already in market, we have requested that Superfish auto-update a fix that addresses these issues,” he added.
As one security researcher pointed out on Twitter, the root certificate remains on the system after uninstalling Superfish and it has to be removed manually, a procedure most average users are not familiar with.
The alternative would be to re-install a stock version of the operating system, since applying the backup image provided by Lenovo contains the Superfish add-on.
.@akatakritos @ETFovac @__apf__ #superfish Yours: http://t.co/JhaE5UqOQJ Mine: http://t.co/F2RXfz8blF Same RSA modulus and SPKI. :|
— Chris Palmer (@fugueish) February 19, 2015
 14 DAY TRIAL //
14 DAY TRIAL //