In a move that bids goodbye and good riddance, both Lenovo and Microsoft have taken measures to eliminate from Windows the root certificate installed by Superfish browser add-on and employed to generate rogue certificates for any website using HTTPS connection.
Superfish has been the target of much criticism lately not necessarily on account of its man-in-the-middle behavior but because it used the same root certificate and RSA private-key encrypting it on all systems.
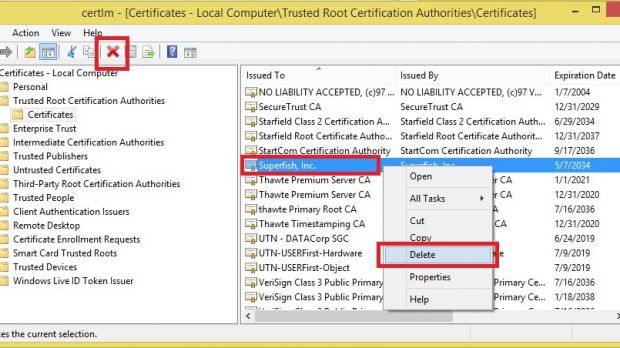
Uninstalling the program does not mitigate the risk
Since the root certificate private-key is available locally, it could be extracted and decrypted, which is exactly what Robert Graham did on Thursday, in about three hours.
The private key of the certificate would allow a malicious actor to carry out their own man-in-the middle attacks through compromised Wi-Fi networks to intercept and to decode the encrypted communication from the client to a server, without raising any suspicion to the victim.
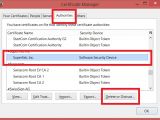
Although the Superfish application can be eliminated from the system by simply uninstalling it, the root certificate persists in Windows’ certificate store and the risk for the user is not mitigated unless it is also removed.
Add-on clings to multiple browsers, creates entries in private certificate stores
Superfish’s purpose is to inject ads in webpages accessed by users and serve them alternative shopping results for the products they look for, based only on the image of the item.
The code of the application itself may not be malicious, but it includes a transparent proxy service (man-in-the-middle) based on Komodia's “SSL Digestor” engine, which is responsible for the creation of non-unique root CA certificates and private keys.
Other products also rely on the SDK from Komodia and intercept traffic in the same way as Superfish does. Among the programs, there are Keep My Family Secure, Qustodio and Kurupira WebFilter, the password for the RSA private key for all of them being the same one, "komodia," as discovered by Graham.
It can get on a computer in multiple ways, and being pushed during the installation process of another program is one of them. However, the method that stirred up the spirits of security researchers was its inclusion in Lenovo consumer notebooks, where its risky traffic interception mechanism was observed.
From September 2014 until January 2015, the add-on came pre-installed on some Lenovo laptops and it was also available in the factory backup image. It would attach itself to any supported browser the user chooses for web navigation, including Firefox, which comes with its own certificate store.
Microsoft and Lenovo to the rescue
To tackle the issue, Microsoft created a signature for its antivirus programs Windows Defender and Security Essentials that includes routines not only for removing Superfish from the system but the root certificate in the OS store as well.
The two antivirus programs are free and built-into Windows versions Vista through 8.1. They act as default protection for the operating system if a third-party solution is not installed.
However, if Firefox is used for browsing, the Superfish certificate would also be injected in its store and would have to be eliminated from there, too. In this case, the removal routines provided by Microsoft would be unsuccessful.
Fortunately, Lenovo has this covered as it was aware that user browsing preferences may extend to Mozilla’s products. As such, the company created and published an automated removal tool that clears the Superfish root certificate in Firefox and Thunderbird certificate stores.
Superfish has been around for many years and users complained about its ad-injection activity multiple times.
Windows Defender version 1.193.444.0 will detect and remove Superfish AND the system cert http://t.co/3Jxz4HMqzQ pic.twitter.com/TqLMtiljuI
— Filippo Valsorda (@FiloSottile) February 20, 2015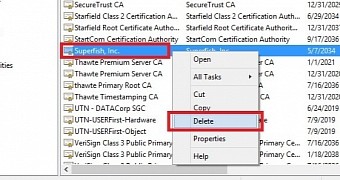
 14 DAY TRIAL //
14 DAY TRIAL //