Lookout researchers came across a new variant of the piece of malware known as Legacy Native, or LeNa. The latest version uses the GingerBreak exploit to gain root access to a device without any user interaction.
While previous variations of LeNa had to rely on the SU utility and some user interaction in order to gain root privileges, thus limiting the potential number of victims to those with rooted devices, the new piece of malware is much more independent.
Basically, devices that aren’t patched against the security hole exploited by GingerBreak are susceptible to an attack.
LeNa hides at the end of a legitimate-looking JPEG image file, where it places a couple of ELF binaries responsible for exploiting the vulnerability and launching the Trojan.
Once on a device, the payload communicates with a remote command and control (C&C) server from which it receives instructions on what to install further and what URLs to display in the web browser.
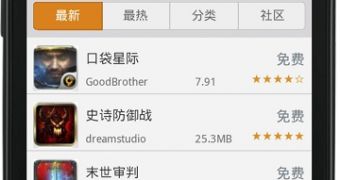
Now there is a single package that LeNa installs and it comes from a Chinese Android application market.
“This package is installed without the user’s knowledge and subsequently launched – the result being that this alternate market may be front-and-center on a device after a user leaves it unattended for a prolonged period of time,” Tim Wyatt from Lookout wrote.
“While it shares much of the same functionality as any mobile application store, this alternate market has not been designed to mimic the official Google Play market.”
For now, experts believe that the Trojan can’t be found on Google Play, but to ensure that your device remains uninfected, be sure to follow these security practices:
- only download applications from trusted sources; - take a look at the permissions requested by an app before installing it; - install a piece of security software specially designed for mobile devices; - always keep an eye out for unusual network activity, inflated phone bills, and any other clues that may indicate the presence of a malicious element.
Note. My Twitter account has been erroneously suspended. While this is sorted out, you can contact me via my author profile or follow me at @EduardKovacs1
 14 DAY TRIAL //
14 DAY TRIAL //