In the last 24 hours many users may have been wondering if they are among the 6.5 million (possibly more) individuals whose LinkedIn passwords have been made public as a result of a possible breach that affected the social media site.
Tech savvy members might have taken their passwords, generated their SHA-1 hashes and compared them with the ones found in the 271-megabyte file posted on the Russian forum.
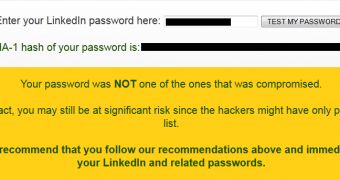
While many are anxiously waiting to see if they receive that dreaded notification email from LinkedIn in which they’re informed that their passwords have been compromised, LastPass provides an easy way for users to learn if they’re on the victims list.
LinkedIn customers simply have to input their passwords into the designated field and press the “test my password” button. A few moments later they know if they’re among the unfortunate ones.
Of course, this test isn’t foolproof because, as Imperva experts have highlighted, the cybercriminals may possess more than 6.5 million passwords. Ars Technica, for instance, reported that around 8 million passcodes may have ended up online.
Getting back to the web tool provided by LastPass, for those who may be concerned that the process isn’t safe and that the company might actually be collecting the passwords entered by users, they should know that only the hashes are sent back to the servers.
“Only the hash of your password will be sent to LastPass.com's servers, not your actual password. This hash will not be stored. Please view source the page if you're technically inclined,” reads a message on the website.
So, if you haven’t already changed your password (on all the accounts that share the same one, not just on LinkedIn), make sure to do it as soon as possible.
 14 DAY TRIAL //
14 DAY TRIAL //