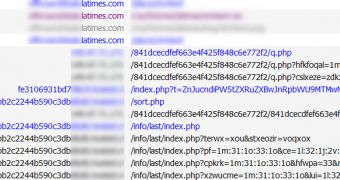
A subdomain of the Los Angeles Times publication has been found to be redirecting users to a website that hosts the notorious BlackHole exploit kit.
Journalist Brian Krebs was among the first to spot the compromised subdomain. Researchers from Avast! Have decided to check it out and they have found that the subdomain has actually been hosting malicious iframes since December 23.
The sites used in the attack are hosted in the US and the Netherlands, but they’re most likely legitimate ones compromised by the cybercriminals.
The experts have analyzed the site to make sure that the results they were seeing were not generated by other factors such as hacker routers, proxies or malicious network drivers.
“After a while, we were pretty sure it is not the case, but most of the automated tools still verified the site as clean. Only by some manual verification we were able to record Fiddler session which clearly shows how the infection runs,” Avast’s Jindřich Kubec explained.
“Because we were getting both the clean replies and also the replies with the malicious iframe inserted, we’re pretty sure we’re seeing the HTTP server with installed malicious module, which changes the file on the fly – they’re unmodified on the disk so that the admins see only clean files and uploading ‘verified clean’ file would not fix anything.”
The module in question was first analyzed by Unmask Parasites and later on by ESET and security researcher Eric Romang.
Avast! attempted to contact LA Times, but they encountered some difficulties, so the malicious redirection was still in place on Friday. Fortunately, their antivirus solutions (and probably the ones provided by other security firms) are capable of blocking the threat.
 14 DAY TRIAL //
14 DAY TRIAL //