Security researchers warn that a new Koobface variant is currently making the rounds on Twitter. However, while the lure remains the same, the underlying social engineering has been improved to make them more credible.
Koobface is one of the first and, at the same time, one of the most successful, social networking worms. It was initially launched on MySpace, but its subsequent variants have targeted Facebook, Bebo, Friendster, hi5, Tagged, and more recently, Twitter.
The worm spreads by using stolen accounts to post spam messages allegedly containing links to online videos. Visiting the link takes unwary users to a Web page displaying a fake embedded video, which is actually just an image. Attempting to view the video will prompt the download of the worm's installer, masquerading as a Flash Player update or special codec.
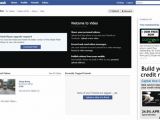
Stefan Tanase, senior security researcher with Kaspersky Lab, has published a breakdown of the changes in the new version, noting that the landing page has changed. "There's a new twist to the social engineering, with links from infected messages leading to a very well designed Facebook lookalike page (far more convincing than the previous YouTube page)," the analyst explains.
The fake Facebook Video page displays an alert, claiming that an upgrade for Flash Player is required. Users familiar with the real online Flash Player update notifications might be tricked into thinking that this warning is legit. The file offered for download is detected by Kaspersky as Net-Worm.Win32.Koobface.d.
Another significant change in this Koobface variant is the use of URL randomization. The URL of the destination page has random tokens appended to it, which are then used to generate unique bit.ly shortened versions.
This method allows each tweet posted via compromised accounts to have its own malicious URL, making harder for Twitter's new filter to keep track of them. Additional randomization is achieved by appending strings such as "HA-HA-HA!!" "W.O.W." "WOW," "L.O.L." "LOL" or ";)" to every offending message, which has the purpose of delaying their identification and removal.
"Currently we’ve identified almost 100 unique IP addresses hosting Koobface," initially noted Mr. Tanase. Fortunately, in a later update, he announced that "the URL which Koobface was spreading from has now been brought down so attacks are blocked."

 14 DAY TRIAL //
14 DAY TRIAL //