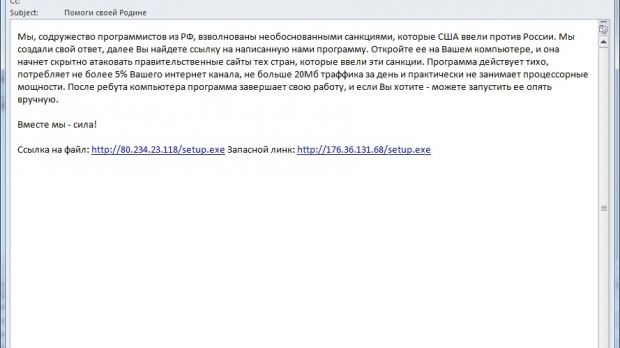
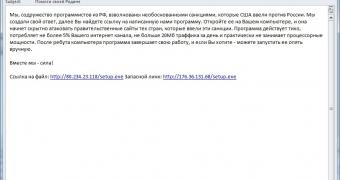
A new malicious campaign has been started against Russian nationals, promoting Kelihos Trojan as a tool for attacking websites under the administration of the US government.
The cybercriminals appeal to the patriotism of Russian citizens to install the malware, deceiving them into thinking that the purpose of the operation is to retaliate against US-imposed sanctions to Russia.
Researchers at Websense, a company providing solutions for protecting organizations from cyber attacks and data theft, discovered that the URL included in the malicious message actually leads to Kelihos Trojan, enslaving the computer of the wannabe cyber-warriors in a botnet controlled by crooks.
Kelihos, also known as Hlux, includes a diverse set of capabilities, such as sending spam, stealing sensitive information, thieving Bitcoin wallets, Bitcoin mining and using the affected computer for distributed denial-of-service (DDoS) attacks.
It also creates a backdoor for the compromised system and can be used to download additional malware on the machine.
Although Kelihos has been the object of multiple take-down operations carried out by law enforcement and private security companies, it has re-spawned, creating new botnets.
According to Websense telemetry, the web pages hosting the malware have been barely accessed, and this campaign may be an attempt to rebuild the botnet.
“What's different about this case is that instead of appealing to the victims' sense of curiosity, the cyber criminals appeal to patriotic sentiments [...], blatantly saying that they will run malware on the intended targets' computers, but without disclosing the true nature of the malware,” say the researchers in a blog post.
Websense says that their systems managed to block over 100,000 malicious emails between August 20 (deployment date) and August 21.
Emails have different subject lines that appeal to the patriotic spirit of the receiver, and the crooks make no effort to disguise the link to the malicious file or the file itself, because they say in the message that an executable file is delivered. All the recipients had email addresses with the .ru top-level domain (TLD).
The malware relies on the WinPcap driver to keep an eye on the web connections and to steal passwords from different protocols, the most targeted one being SMTP, probably to increase the distribution rate by using the infected computer to deliver spam, Websense says.
“When run on the victims' computers, the bot contacts the Command & Control (C2) infrastructure over TCP, then sends an encrypted GET request to the C2 URLs (hosted in Russia and Ukraine),” explain the security experts.
In some of the messages encountered by the security firm, the crooks also provide tips to disable the antivirus solution on the system, to allow installation of the malware.
This is an out of ordinary method to deliver malware, but it may also be very efficient, preying on the citizen’s willingness to participate in a retribution campaign against actors that took measures, political or otherwise, against their country.
 14 DAY TRIAL //
14 DAY TRIAL //