Kaspersky Lab has released the second part of the report on Red October, the 5-year-long cyber espionage campaign that’s believed to be one of the most sophisticated cybercriminal operations to target government, diplomatic and research organizations.
Since the campaign itself is so sophisticated, the second part of the paper that covers it – which focuses on the modules used by the attackers – comprises over 140 pages of technical analysis.
In order to perform a detailed analysis of Red October, Kaspersky experts set up several fake victims worldwide.
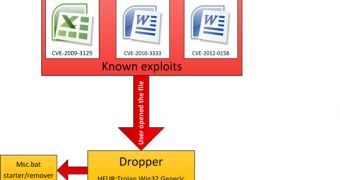
The attacks start with a cleverly designed spear phishing email that contains an attachment in the form of an Excel or a Word document.
When they’re opened, an exploit is triggered and the dropper is extracted and executed. The dropper module is also responsible for creating the loader module, a PE EXE file compiled in Microsoft Visual Studio 2005.
This loader decrypts a file that contains the main payload.
Once everything is set in place, the attackers can start using the large number of modules to perform various tasks.
The modules can help the cybercriminals achieve two types of tasks: persistent and one-time tasks.
The persistent ones include waiting for a USB drive to be connected to the infected computer to steal files (including deleted files), and retrieving information from iPhone and Nokia phones or ones running Windows Phone when they’re connected.
Persistent tasks also include logging keystrokes, stealing emails from Microsoft Outlook and other mail servers, and executing malicious payloads embedded in Office or PDF documents.
The one-time tasks include collecting general hardware and software information, collecting file system and network details, extracting history from popular browsers, or harvesting saved passwords, Windows account hashes, and Outlook account information.
 14 DAY TRIAL //
14 DAY TRIAL //