Russian-based security company Kaspersky Lab discovered recently that a powerful and mysterious advanced persistent threat (APT) group known as Duqu penetrated some of its internal systems using a zero-day in the Windows Kernel.
Cyber activity associated with Duqu cyber-espionage platform has not been recorded since 2012 and it was believed that the attacker no longer relied on the toolset for its operations.
However, infections from a new version of the platform (dubbed Duqu 2) emerged in 2014 and continued to be recorded in 2015 in western countries, the Middle East and Asia.
Windows zero-day wielded against security firm
The zero-day vulnerability leveraged by the threat actor is CVE-2015-2360, patched by Microsoft on Tuesday via the monthly release of its security updates. Kaspersky says that up to two other security issues may have been used in the attack on its systems.
Researchers say that the initial attack started at one of its smaller offices in the Asia-Pacific region and it probably involved spear-phishing emails.
In attacks on other victims monitored by Kaspersky, after penetration, the threat actor moved laterally via another zero-day at that time (CVE-2014-6324, patched in November 2014), which allowed the credentials of an unprivileged user to be elevated to a domain administrator account; this way, other computers on the same domain could be compromised.
“Malicious modules were also observed performing a ‘pass the hash’ attack inside the local network, effectively giving the attackers many different ways to do lateral movement,” Kaspersky says in a report released on Wednesday.
Over 100 variants of malicious plugins identified
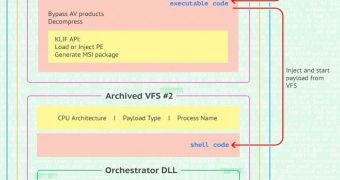
Duqu 2 uses multiple tactics to spread on the network, and in most cases, the attack was carried out by deploying Microsoft Windows Installer Packages (MSI) and launching them remotely to other hosts.
The MSI files could load into the memory of the machine payloads they included for backdoor access and for espionage purposes.
Kaspersky says that the packages can contain multiple modules for different spying functions. Compared to the backdoor functionality, these bundles can have a size as large as 18MB. Over 100 variants of this type of plugins have been identified during the investigation of the attack.
The main module in Duqu 2 implements handlers for communication with the command and control (C&C) server over multiple protocols using a proxy connection and a self-signed HTTPS certificate.
Spying seems to be the main purpose of the attack
The purpose of the assault on Kaspersky’s network seems to be spying on the technology used and developed by company, current researches conducted by the security experts, and internal processes.
Analysis of the malware showed that it could collect data regarding running processes, active desktop and terminal sessions, as well as search and exfiltrate files matching certain rules (“*.inuse, *.hml,” filename contains “data.hmi” or “val.dat,” as well as content from specific folders).
Additional functionality included listing files in directories, uploading and downloading arbitrary files, and reading and writing content in the files.
A network infection module was discovered trying to steal tokens from running processes initiated by a logged-on user with domain admin rights in order get administrative credentials ; then, it attempted to connect to the targeted machine via Windows shares.
Variants of Duqu 2 modules discovered by the researchers included functions for stealing passwords from different software products, like web browsers, remote desktop solutions or online accounts.
Malicious components run in system memory
The malware platform was conceived to survive in the memory of the compromised systems by targeting servers with high-uptime and then re-infecting the machines that would go through a restart, an action that eliminated the malware pieces.
One reason for this form of persistence can be accounted by the fact that the threat actor did not want to draw attention to the compromise.
Attackers leave false flags behind to prevent attribution
Attribution of the attack is not simple, especially in the case of an APT. Kaspersky found several false flags in the malware code, which point to hackers from China and Romania, as well as to the operators of the MiniDuke campaign identified in early 2013.
“From a threat actor point of view, the decision to target a world-class security company must be quite difficult. On one hand, it almost surely means the attack will be exposed - it’s very unlikely that the attack will go unnoticed. So the targeting of security companies indicates that either they are very confident they won’t get caught, or perhaps they don’t care much if they are discovered and exposed,” Kaspersky said, adding that the disclosure of the attack on them is part of their commitment to transparency.
The company is confident that the compromise does not have repercussions on its products, technologies and services, and that its customers and partners are safe.
 14 DAY TRIAL //
14 DAY TRIAL //