Shortly after the world learned of the existence of the Flame malware, security experts from Kaspersky rushed not only to analyze the threat, but also to remove the risks it posed.
Collaborating with GoDaddy’s Network Abuse Department and OpenDNS’s security research team, Kaspersky has managed to sinkhole most of the malicious domains utilized by the malware as command and control (C&C) servers.
If we were to compare Flame to Duqu, a piece of malware that many experts have named as being similar, we find that one of the most significant differences is that the former uses SSH connections for data exfiltration, not only SSL.
As far as the domains that belong to the Flame C&C infrastructure are concerned, experts have found a number of 80 different ones, all registered with fake identities at various registrars.
The addresses that allegedly belong to the domain owners are actually the locations of hotels, shops, organizations, doctor’s offices, and, in some cases, places that don’t exist at all.
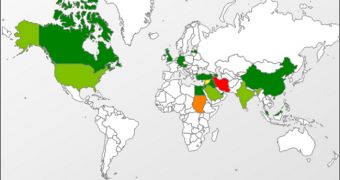
When referring to Flame’s victims, the security firm reveals that around 185 are from Iran, 95 from Israel and Palestine, 32 from Sudan, 29 from Syria, and 11 from the US.
An important observation made by the experts is the fact that even though most of the infected devices run a Windows 7 32 bit operating system, the malware is not able to operate on Windows 7 64 bit, this variant being recommended as a good solution against such threats.
Similar to Duqu, Flame also seems to have a big appetite for AutoCad drawings. In addition, PDF, text files and other documents are all on the list of extracted data. To upload the data to the C&C servers, the malware’s masterminds simply compress them using the open source Zlib and a modified variant of the PPDM compression libraries.
Finally, Kaspersky advises CERT Institutions to reach out to them in case they need any assistance in dealing with Flame.
 14 DAY TRIAL //
14 DAY TRIAL //